Penetration testing experts are crucial for safeguarding an organization's cybersecurity. They identify vulnerabilities and simulate cyber attacks to ensure that defenses are both effective and resilient.
Skills required for this role include a deep understanding of network security, proficiency in various hacking tools, and a strong analytical mindset. Additionally, soft skills such as communication and problem-solving are essential.
Candidates can write these abilities in their resumes, but you can’t verify them without on-the-job Penetration Testing Expert skill tests.
In this post, we will explore 8 essential Penetration Testing Expert skills, 8 secondary skills and how to assess them so you can make informed hiring decisions.
Table of contents
8 fundamental Penetration Testing Expert skills and traits
The best skills for Penetration Testing Experts include Network Analysis, Ethical Hacking, Cryptography, Scripting Languages, Web Application Security, System Exploitation, Threat Modeling and Compliance Knowledge.
Let’s dive into the details by examining the 8 essential skills of a Penetration Testing Expert.
Network Analysis
A penetration testing expert uses network analysis to identify vulnerabilities within the network infrastructure. This skill involves monitoring network traffic, understanding protocols, and detecting anomalies that could indicate security breaches.
For more insights, check out our guide to writing a Network Engineer Job Description.
Ethical Hacking
Ethical hacking is the practice of simulating cyber attacks to identify security weaknesses. Penetration testers use this skill to help organizations strengthen their defenses by proactively finding and fixing security vulnerabilities.
Cryptography
Understanding cryptography is crucial for a penetration testing expert as it involves securing information by transforming it into secure formats. This skill is used to test the strength of encryption algorithms and ensure data integrity and confidentiality.
Scripting Languages
Knowledge of scripting languages such as Python, Bash, or PowerShell is essential for automation and efficiency in testing processes. Penetration testers use these skills to write custom scripts that automate repetitive tasks and exploit vulnerabilities.
Web Application Security
Penetration testers must be adept at assessing the security of web applications. This includes understanding web protocols, session management, and application vulnerabilities to prevent attacks such as SQL injection and cross-site scripting.
System Exploitation
This skill involves the ability to exploit vulnerabilities in systems to gain unauthorized access. Penetration testers use this skill to demonstrate potential entry points and the impact of an exploit in a controlled and safe manner.
Threat Modeling
Threat modeling is used by penetration testers to identify, quantify, and prioritize potential threats in software applications and networks. This proactive approach helps in focusing their efforts on the most significant threats.
Compliance Knowledge
Understanding various compliance requirements like GDPR, HIPAA, or PCI-DSS is necessary for a penetration testing expert. This knowledge ensures that security assessments align with legal and regulatory standards.
8 secondary Penetration Testing Expert skills and traits
The best skills for Penetration Testing Experts include Social Engineering, Wireless Security, Digital Forensics, Reverse Engineering, Cloud Security, Physical Security, Incident Response and Security Auditing.
Let’s dive into the details by examining the 8 secondary skills of a Penetration Testing Expert.
Social Engineering
This involves manipulating individuals into breaking normal security procedures. It's a useful skill for penetration testers to understand how human factors can be exploited to gain access to secure systems.
Wireless Security
Penetration testers need to understand the vulnerabilities associated with wireless networks. This includes securing Wi-Fi networks and protecting against threats like rogue access points.
Digital Forensics
This skill involves the recovery and investigation of material found in digital devices, often used post-breach to determine the cause and extent of an attack. Useful for penetration testers in understanding attack vectors and consequences.
Reverse Engineering
Reverse engineering is the process of deconstructing software or systems to understand their functioning. This skill helps penetration testers find hidden vulnerabilities that are not apparent in normal testing.
Cloud Security
With the rise of cloud computing, understanding cloud security is important for penetration testers. This involves securing cloud environments and knowing cloud-specific vulnerabilities and mitigation strategies.
Physical Security
Often overlooked, physical security plays a crucial role in comprehensive security testing. Penetration testers sometimes need to assess the physical measures in place to prevent unauthorized access to facilities.
Incident Response
Ability to respond to security breaches effectively is a valuable skill. Penetration testers with this skill can help organizations plan and execute appropriate responses to security incidents.
Security Auditing
This involves the systematic evaluation of security of a company's information system by measuring how well it conforms to a set of established criteria. A useful skill for penetration testers in assessing ongoing security measures.
How to assess Penetration Testing Expert skills and traits
Assessing the skills and traits of a Penetration Testing Expert can be a challenging task. It's not just about knowing the technical skills but also understanding how they apply them in real-world scenarios. While resumes can list qualifications and certifications, they don't provide a complete picture of a candidate's proficiency and practical experience.
To confidently gauge a candidate's competencies, skills-based hiring practices, such as talent assessments, are essential. These assessments can help you evaluate key skills like Network Analysis, Ethical Hacking, Cryptography, Scripting Languages, Web Application Security, System Exploitation, Threat Modeling, and Compliance Knowledge. Adaface on-the-job skill tests can help you achieve a 2x improved quality of hires and an 85% reduction in screening time.
Let’s look at how to assess Penetration Testing Expert skills with these 6 talent assessments.
Network Engineer Online Test
Our Network Engineer Online Test evaluates candidates on a wide range of networking topics, from network protocols and security to routing, switching, and network performance optimization.
The test assesses technical knowledge in network design, management, troubleshooting, and the use of TCP/IP in LAN/WAN environments.
Candidates who perform well demonstrate a strong ability to design, implement, and maintain complex network infrastructures and resolve network issues effectively.
Ethical Hacking Test
Our Ethical Hacking Test focuses on a candidate's skills in ethical hacking, including cyber security, network security, and web application security.
This test challenges candidates to identify vulnerabilities, exploit security flaws, and apply knowledge in cyber security and network security to provide effective solutions.
Successful candidates will have proven abilities to prevent unauthorized access and protect sensitive information across various platforms.
Cryptography Test
The Cryptography Test assesses a candidate's understanding of cryptography algorithms like RSA, digital signatures, and hashing techniques.
Candidates are tested on their ability to apply cryptography concepts, including encoding and decoding, within the context of cyber security fundamentals.
High-scoring individuals demonstrate a deep understanding of securing digital communications and data integrity.
Python Online Test
Our Python Online Test evaluates candidates on Python programming, covering data structures, error handling, and object-oriented programming.
The assessment includes scenario-based questions on scripting, web scraping, and database manipulation using Python.
Candidates excelling in this test show strong problem-solving skills and the ability to write clean, efficient code.
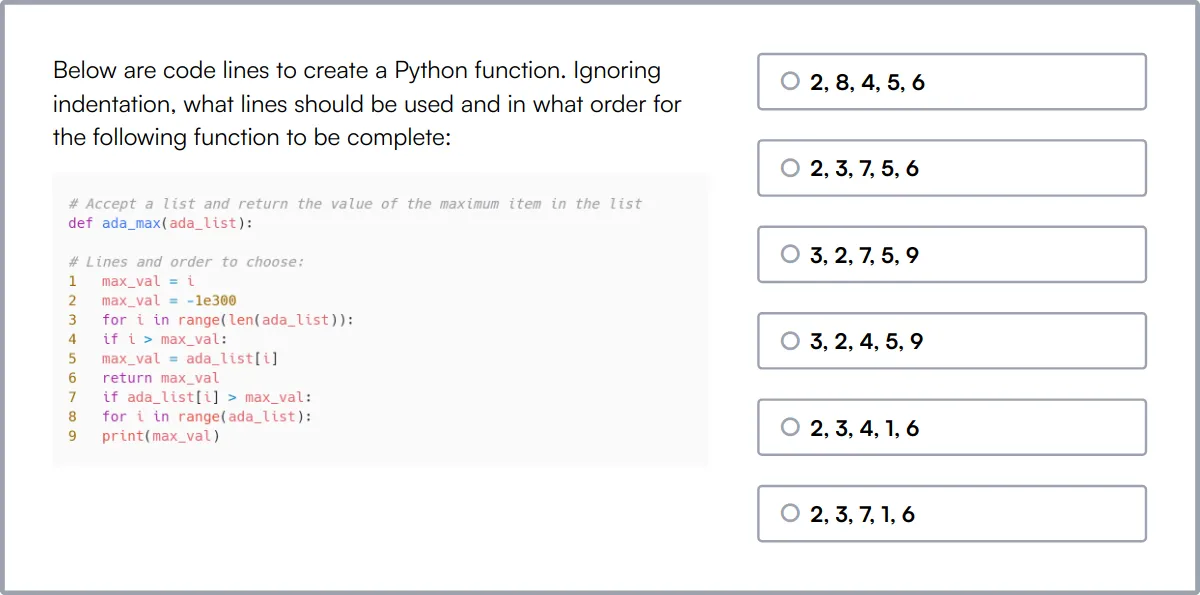
Penetration Testing Test
The Penetration Testing Test measures expertise in penetration testing, vulnerability assessment, and network security.
This test evaluates the candidate's skills in identifying and ethically exploiting vulnerabilities to improve system and application security.
Top performers are adept at providing actionable recommendations to enhance the security posture of the systems tested.
GDPR Online Test
Our GDPR Online Test assesses understanding of GDPR regulations, focusing on data protection, privacy, and security.
The test evaluates candidates on their ability to develop and implement GDPR compliance policies and manage data protection risks.
Candidates who score well are proficient in ensuring the security and privacy of personal data, complying with data protection regulations.
Summary: The 8 key Penetration Testing Expert skills and how to test for them
| Penetration Testing Expert skill | How to assess them |
|---|---|
| 1. Network Analysis | Evaluate the ability to monitor and analyze network traffic. |
| 2. Ethical Hacking | Assess skills in identifying and exploiting security vulnerabilities. |
| 3. Cryptography | Test knowledge of encryption algorithms and secure communication methods. |
| 4. Scripting Languages | Check proficiency in writing scripts for automation and testing. |
| 5. Web Application Security | Gauge expertise in identifying and mitigating web-based threats. |
| 6. System Exploitation | Measure capability to exploit system vulnerabilities and gain unauthorized access. |
| 7. Threat Modeling | Evaluate skills in identifying and prioritizing potential security threats. |
| 8. Compliance Knowledge | Assess understanding of regulatory requirements and industry standards. |
Penetration Testing Test
Penetration Testing Expert skills FAQs
What skills are essential for a Penetration Testing Expert?
Key skills include Network Analysis, Ethical Hacking, Cryptography, Scripting Languages, Web Application Security, and System Exploitation.
How can recruiters assess a candidate's Network Analysis skills?
Recruiters can use practical tests that involve analyzing network traffic, identifying vulnerabilities, and suggesting mitigation strategies.
What is the importance of Ethical Hacking in penetration testing?
Ethical Hacking helps identify and fix security vulnerabilities before malicious hackers can exploit them, ensuring the safety of systems and data.
How can a candidate's proficiency in Scripting Languages be evaluated?
Proficiency can be assessed through coding challenges that require writing scripts to automate security tasks or exploit vulnerabilities.
Why is Web Application Security critical for penetration testers?
Web Application Security is crucial because web applications are common targets for attacks, and securing them helps protect sensitive data and user privacy.
What methods can be used to test a candidate's Social Engineering skills?
Simulated phishing attacks and role-playing scenarios can be used to evaluate a candidate's ability to recognize and counter social engineering tactics.
How do you assess a candidate's knowledge in Cloud Security?
Assess their understanding of cloud security principles, common vulnerabilities, and best practices through scenario-based questions and practical tests.
What role does Digital Forensics play in penetration testing?
Digital Forensics helps in investigating security breaches, understanding attack vectors, and gathering evidence to improve future security measures.
Assess and hire the best Penetration Testing Experts with Adaface
Assessing and finding the best Penetration Testing Expert is quick and easy when you use talent assessments. You can check out our product tour, sign up for our free plan to see talent assessments in action or view the demo here:

40 min skill tests.
No trick questions.
Accurate shortlisting.
We make it easy for you to find the best candidates in your pipeline with a 40 min skills test.
Try for freeRelated posts
Free resources



