Cyber Security Engineers are at the forefront of protecting digital infrastructures from a range of cyber threats. They ensure the security of data and networks against breaches and attacks, playing a critical role in safeguarding an organization's information assets.
The role requires a deep understanding of network security, system vulnerabilities, and encryption technologies. Additionally, skills in problem-solving, analytical thinking, and effective communication are indispensable for success in this field.
Candidates can write these abilities in their resumes, but you can’t verify them without on-the-job Cyber Security Engineer skill tests.
In this post, we will explore 9 essential Cyber Security Engineer skills, 11 secondary skills and how to assess them so you can make informed hiring decisions.
Table of contents
9 fundamental Cyber Security Engineer skills and traits
The best skills for Cyber Security Engineers include Network Security, Cryptography, Incident Response, Vulnerability Assessment, Penetration Testing, Security Information and Event Management (SIEM), Firewall Management, Malware Analysis and Identity and Access Management (IAM).
Let’s dive into the details by examining the 9 essential skills of a Cyber Security Engineer.
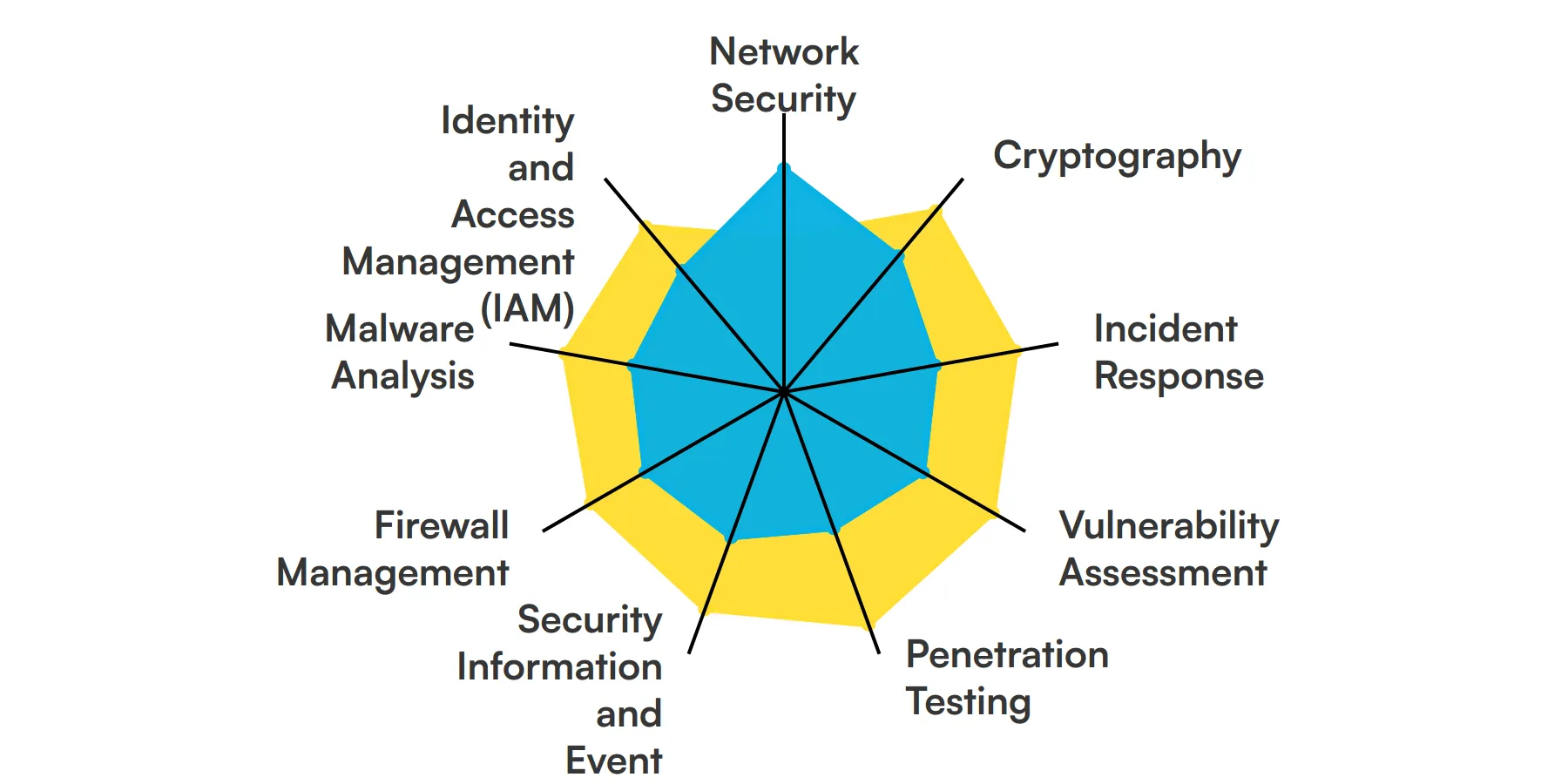
Network Security
Understanding network security is crucial for a Cyber Security Engineer. This skill involves protecting the integrity, confidentiality, and availability of data as it is transmitted across or accessed through networks. Engineers use this knowledge to design and implement secure network architectures, monitor for suspicious activity, and respond to security breaches.
For more insights, check out our guide to writing a Network Engineer Job Description.
Cryptography
Cryptography is the practice of securing information by transforming it into an unreadable format. Cyber Security Engineers use cryptographic techniques to protect sensitive data from unauthorized access. This includes implementing encryption algorithms, managing cryptographic keys, and ensuring secure communication channels.
Incident Response
Incident response involves identifying, managing, and mitigating security breaches or cyber attacks. Cyber Security Engineers must be adept at quickly analyzing incidents, containing threats, and restoring normal operations. This skill is essential for minimizing damage and preventing future incidents.
Vulnerability Assessment
Vulnerability assessment is the process of identifying, quantifying, and prioritizing security weaknesses in systems. Cyber Security Engineers conduct regular assessments to discover potential vulnerabilities that could be exploited by attackers. This proactive approach helps in strengthening the overall security posture.
Penetration Testing
Penetration testing, or ethical hacking, involves simulating cyber attacks to identify and fix security weaknesses. Cyber Security Engineers use this skill to test the effectiveness of security measures and ensure that systems are resilient against real-world threats. It’s a hands-on way to validate security controls.
Security Information and Event Management (SIEM)
SIEM involves collecting, analyzing, and responding to security-related data from various sources. Cyber Security Engineers use SIEM tools to gain insights into potential security threats, monitor for unusual activities, and automate incident response. This helps in maintaining a robust security environment.
Firewall Management
Firewalls are critical for protecting networks from unauthorized access. Cyber Security Engineers must be skilled in configuring and managing firewalls to control incoming and outgoing network traffic based on predetermined security rules. This helps in preventing malicious activities and safeguarding sensitive data.
Malware Analysis
Malware analysis involves examining malicious software to understand its behavior, origin, and impact. Cyber Security Engineers use this skill to detect, analyze, and mitigate malware threats. This knowledge is essential for developing effective defense strategies and protecting systems from infections.
Identity and Access Management (IAM)
IAM is the process of managing user identities and their access to resources. Cyber Security Engineers implement IAM solutions to ensure that only authorized users can access sensitive information. This involves setting up authentication mechanisms, managing user permissions, and monitoring access activities.
11 secondary Cyber Security Engineer skills and traits
The best skills for Cyber Security Engineers include Programming, Operating Systems, Cloud Security, Data Analysis, Compliance and Regulations, Forensics, Threat Intelligence, DevSecOps, Social Engineering Awareness, Wireless Security and SIEM Tools.
Let’s dive into the details by examining the 11 secondary skills of a Cyber Security Engineer.
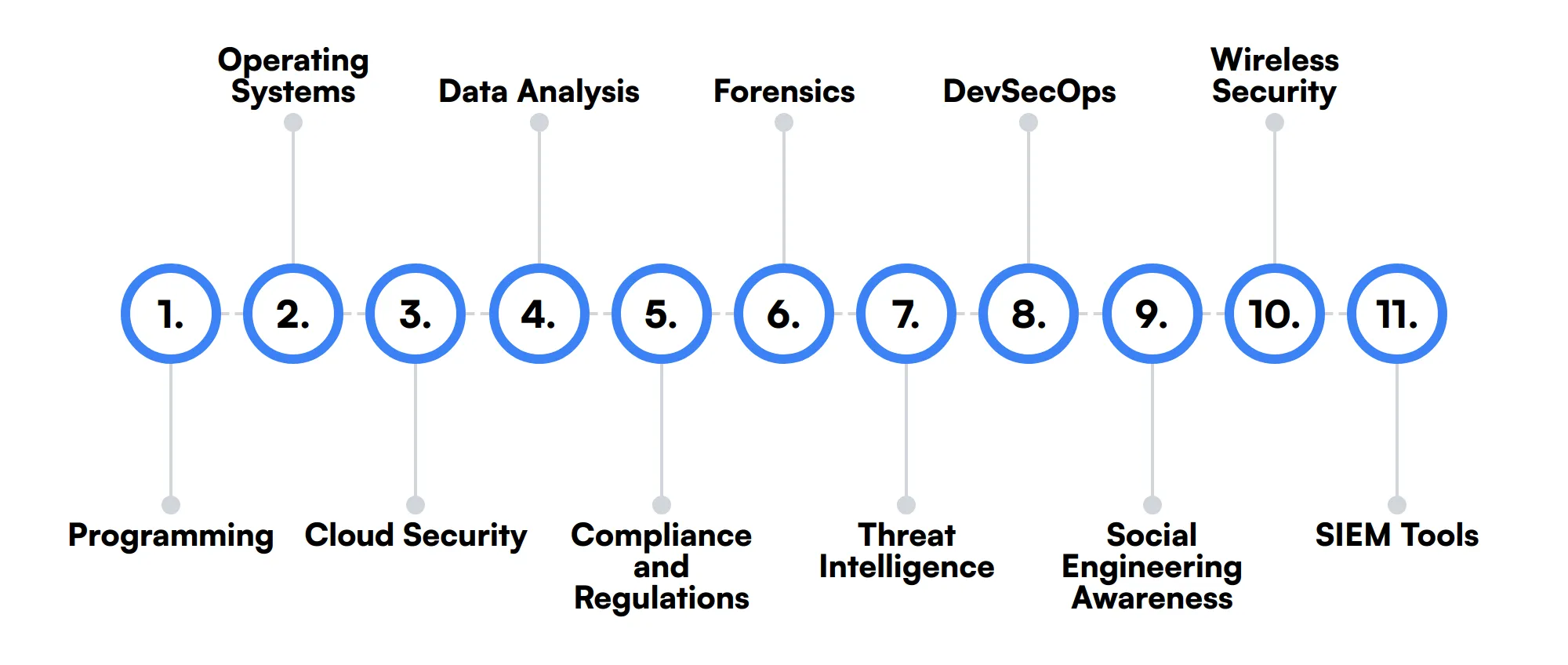
Programming
Programming skills are valuable for automating security tasks, developing security tools, and analyzing code for vulnerabilities. Languages like Python, C++, and Java are commonly used in the field.
Operating Systems
Knowledge of various operating systems, including Windows, Linux, and macOS, is important for understanding how different systems can be secured and where vulnerabilities might exist.
Cloud Security
As organizations move to the cloud, understanding cloud security principles is essential. This includes securing cloud infrastructure, managing cloud-based services, and ensuring compliance with cloud security standards.
Data Analysis
Data analysis skills help in interpreting security data, identifying trends, and making informed decisions. Cyber Security Engineers use data analysis to detect anomalies and predict potential security threats.
Compliance and Regulations
Understanding compliance requirements and regulations, such as GDPR, HIPAA, and PCI-DSS, is important for ensuring that security practices meet legal and industry standards.
Forensics
Forensic skills involve investigating cyber incidents to determine the cause and impact. This includes collecting and analyzing digital evidence, which is crucial for legal proceedings and improving security measures.
Threat Intelligence
Threat intelligence involves gathering and analyzing information about potential threats. Cyber Security Engineers use this information to anticipate and defend against cyber attacks.
DevSecOps
DevSecOps integrates security practices into the software development lifecycle. Cyber Security Engineers work with development teams to ensure that security is considered at every stage of development.
Social Engineering Awareness
Understanding social engineering tactics helps in recognizing and preventing attacks that exploit human psychology. This includes phishing, pretexting, and other manipulation techniques.
Wireless Security
Securing wireless networks is important to prevent unauthorized access and data breaches. This involves configuring secure wireless protocols, monitoring for rogue access points, and implementing strong encryption.
SIEM Tools
Familiarity with various SIEM tools, such as Splunk, ArcSight, and QRadar, is beneficial for monitoring and managing security events. These tools help in detecting and responding to security incidents effectively.
How to assess Cyber Security Engineer skills and traits
Assessing the skills and traits of a Cyber Security Engineer involves more than just glancing at their resume. It's about understanding how well they can handle real-world security challenges across various domains such as network security, cryptography, and incident response.
While certifications and past experiences provide a snapshot, they do not fully reveal a candidate's ability to adapt and respond to evolving threats. To truly assess these skills, practical and scenario-based evaluations are necessary.
Adaface assessments offer a tailored approach to evaluating the competencies of Cyber Security Engineers. By simulating real-life problems that require knowledge in areas like penetration testing, vulnerability assessment, and malware analysis, these tests ensure that candidates are not only knowledgeable but also capable of applying their skills effectively. Learn more about Adaface assessments here.
Using these assessments can help streamline the hiring process, potentially reducing screening time by up to 85%, ensuring that you focus only on the most capable candidates.
Let’s look at how to assess Cyber Security Engineer skills with these 4 talent assessments.
CISCO Security Online Test
Our CISCO Security Online Test evaluates candidates on their understanding of network security concepts and Cisco network security products and solutions. The test covers skills such as CISCO Firewall, CISCO IPS/IDS, and CISCO VPN.
The test assesses their knowledge of security technologies like firewall, VPN, intrusion prevention, and content security. It also evaluates their ability to design and implement secure network architectures using Cisco products.
Successful candidates demonstrate a strong understanding of network threats and vulnerabilities, access control and identity management, and security policies and best practices.
Cryptography Test
Our Cryptography Test evaluates a candidate's knowledge of cryptography concepts, network engineering, and cyber security. The test covers skills such as digital signatures, cryptography algorithms, and hashing techniques.
The test assesses their understanding of encoding and decoding, cyber security fundamentals, and various cryptographic algorithms like RSA. It also evaluates their ability to apply these concepts in real-world scenarios.
High-scoring candidates show proficiency in digital signatures and hashing techniques, demonstrating their ability to secure data and communications.
Penetration Testing Test
Our Penetration Testing Test evaluates a candidate's knowledge and skills in penetration testing, network security, vulnerability assessment, and web application security. The test covers skills such as ethical hacking and vulnerability identification.
The test assesses their ability to identify vulnerabilities, exploit them ethically, and provide recommendations for improving the security posture of systems and applications. It also evaluates their understanding of network security and web application security.
Successful candidates demonstrate strong skills in vulnerability assessment and penetration testing, showing their ability to enhance the security of systems and applications.
Elasticsearch Test
Our Elasticsearch Test evaluates candidates' ability to design and deploy Elasticsearch clusters, configure and optimize search queries, and manage data ingestion and indexing. The test covers skills such as data modeling, mapping, and aggregations.
The test assesses their understanding of data indexing, search queries, and document retrieval. It also evaluates their ability to manage cluster management, performance optimization, and security.
High-scoring candidates demonstrate proficiency in scaling and distribution, monitoring and troubleshooting, and integration with other systems.
Summary: The 9 key Cyber Security Engineer skills and how to test for them
| Cyber Security Engineer skill | How to assess them |
|---|---|
| 1. Network Security | Evaluate ability to secure a network against unauthorized access and threats. |
| 2. Cryptography | Test knowledge of encryption techniques and their application in security. |
| 3. Incident Response | Assess skills in managing and mitigating security breaches or threats. |
| 4. Vulnerability Assessment | Check capability to identify and evaluate system vulnerabilities. |
| 5. Penetration Testing | Determine proficiency in ethical hacking to find security weaknesses. |
| 6. Security Information and Event Management (SIEM) | Review expertise in managing security events and logs with SIEM tools. |
| 7. Firewall Management | Gauge ability to configure and manage firewall settings effectively. |
| 8. Malware Analysis | Evaluate skills in identifying and analyzing malicious software. |
| 9. Identity and Access Management (IAM) | Assess management of user identities and access controls. |
Cyber Security Assessment Test
Cyber Security Engineer skills FAQs
What are the key skills required for a Cyber Security Engineer?
Cyber Security Engineers should be proficient in network security, cryptography, and incident response. They also need skills in vulnerability assessment, penetration testing, and SIEM. Additional expertise in firewall management, malware analysis, and IAM is beneficial.
How can recruiters assess the proficiency in network security for a candidate?
Recruiters can assess network security skills by reviewing candidates' experience with firewall configurations, VPN management, and intrusion detection systems. Practical tests or case studies during interviews can also provide insight into their hands-on abilities.
What is the importance of programming skills in cyber security?
Programming skills enable Cyber Security Engineers to automate security solutions, analyze malware, and develop tools that enhance security. Languages like Python, Bash, or PowerShell are commonly used in this field.
How does knowledge of compliance and regulations impact a Cyber Security Engineer's role?
Understanding compliance and regulations is critical as it ensures that security measures align with legal and industry standards. This knowledge helps in implementing security frameworks that protect organizational data and avoid legal penalties.
What role does threat intelligence play in cyber security?
Threat intelligence involves analyzing and understanding potential threats to preemptively defend against them. It helps Cyber Security Engineers stay ahead of emerging threats and tailor their security strategies accordingly.
Why is social engineering awareness necessary for Cyber Security Engineers?
Social engineering awareness is necessary because many security breaches start with human errors or deception. Training in this area helps engineers to design systems and protocols that minimize the risk of such breaches.
How can penetration testing skills be assessed during the hiring process?
Assessing penetration testing skills can be done through practical exams where candidates demonstrate their ability to identify and exploit system vulnerabilities. Reviewing past projects or certifications like OSCP can also indicate proficiency.
What is the significance of SIEM tools in a Cyber Security Engineer's toolkit?
SIEM tools are significant as they provide real-time analysis of security alerts generated by applications and network hardware. They help engineers in quick detection, analysis, and response to security incidents.

40 min skill tests.
No trick questions.
Accurate shortlisting.
We make it easy for you to find the best candidates in your pipeline with a 40 min skills test.
Try for freeRelated posts
Free resources



