Cyber Security Analysts are the guardians of an organization's digital assets. They protect sensitive information from cyber threats, ensuring the integrity, confidentiality, and availability of data across networks and systems.
Cyber security skills include knowledge of network security, threat analysis, and incident response, as well as abilities like critical thinking and attention to detail.
Candidates can write these abilities in their resumes, but you can’t verify them without on-the-job Cyber Security Analyst skill tests.
In this post, we will explore 9 essential Cyber Security Analyst skills, 11 secondary skills and how to assess them so you can make informed hiring decisions.
Table of contents
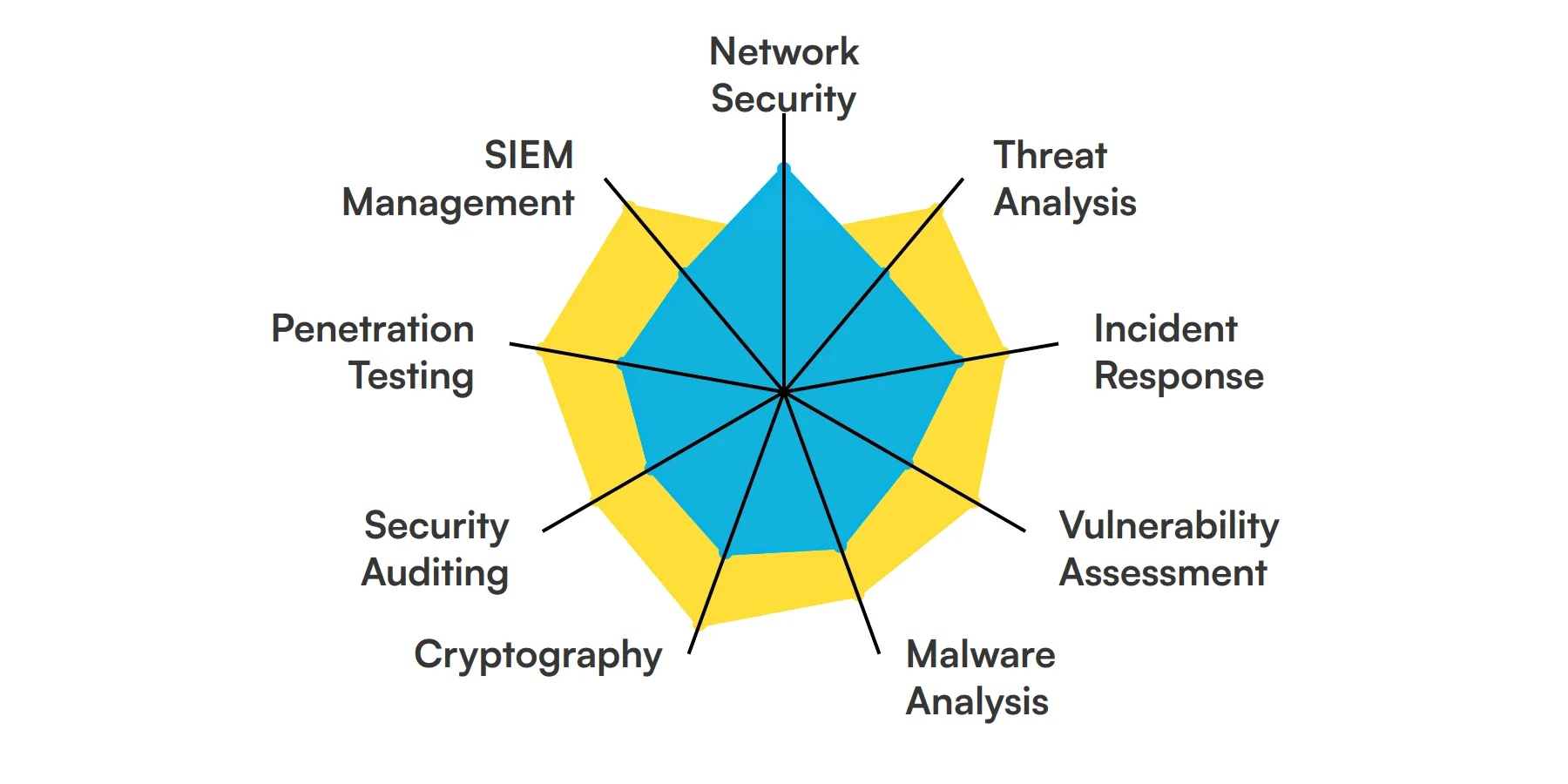
9 fundamental Cyber Security Analyst skills and traits
The best skills for Cyber Security Analysts include Network Security, Threat Analysis, Incident Response, Vulnerability Assessment, Malware Analysis, Cryptography, Security Auditing, Penetration Testing and SIEM Management.
Let’s dive into the details by examining the 9 essential skills of a Cyber Security Analyst.
Network Security
Understanding network security is crucial for a Cyber Security Analyst. This skill involves protecting the integrity, confidentiality, and availability of data as it is transmitted across or accessed through networks. Analysts use this knowledge to identify vulnerabilities and implement measures to prevent unauthorized access.
For more insights, check out our guide to writing a Network Engineer Job Description.
Threat Analysis
Threat analysis involves identifying and evaluating potential threats to an organization's information systems. Cyber Security Analysts use this skill to anticipate and mitigate risks before they can be exploited by malicious actors. This proactive approach helps in maintaining the security posture of the organization.
Incident Response
Incident response is the process of handling and managing security breaches or attacks. Cyber Security Analysts must be adept at quickly identifying, containing, and mitigating incidents to minimize damage. This skill ensures that the organization can recover swiftly and learn from security events.
Check out our guide for a comprehensive list of interview questions.
Vulnerability Assessment
Vulnerability assessment involves identifying, quantifying, and prioritizing vulnerabilities in a system. Cyber Security Analysts use this skill to conduct regular scans and tests to find weaknesses that could be exploited. This helps in strengthening the overall security framework.
Malware Analysis
Malware analysis is the study of malicious software to understand its behavior, origin, and impact. Cyber Security Analysts use this skill to dissect malware, understand its mechanisms, and develop strategies to defend against similar threats in the future.
For more insights, check out our guide to writing a Cyber Security Analyst Job Description.
Cryptography
Cryptography is the practice of securing information by transforming it into an unreadable format. Cyber Security Analysts use cryptographic techniques to protect sensitive data from unauthorized access and ensure secure communication channels.
Security Auditing
Security auditing involves reviewing and assessing an organization's security policies and procedures. Cyber Security Analysts use this skill to ensure compliance with regulations and standards, identify gaps, and recommend improvements to enhance security measures.
Penetration Testing
Penetration testing, or ethical hacking, involves simulating cyber attacks to identify vulnerabilities. Cyber Security Analysts use this skill to test the effectiveness of security measures and uncover weaknesses that need to be addressed.
SIEM Management
Security Information and Event Management (SIEM) involves collecting and analyzing security data from various sources. Cyber Security Analysts use SIEM tools to monitor, detect, and respond to security incidents in real-time, ensuring a robust defense mechanism.
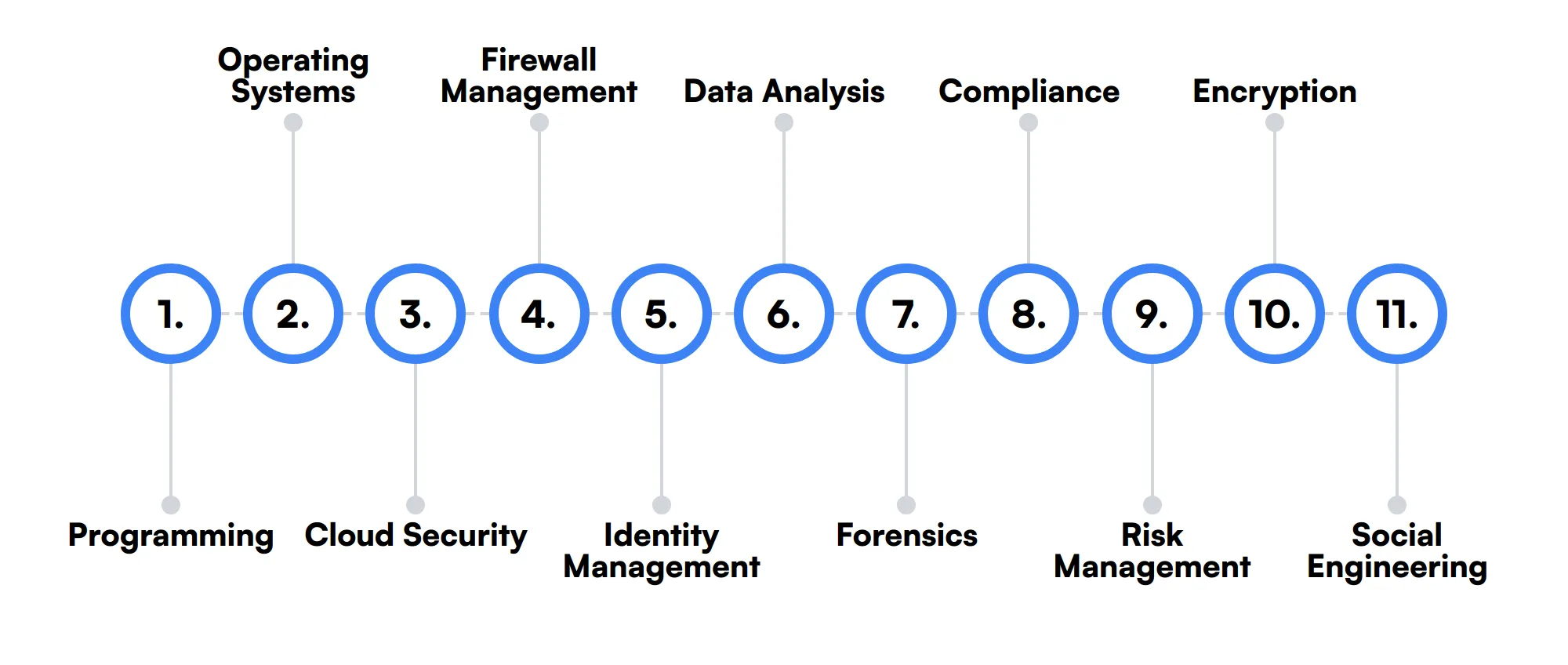
11 secondary Cyber Security Analyst skills and traits
The best skills for Cyber Security Analysts include Programming, Operating Systems, Cloud Security, Firewall Management, Identity Management, Data Analysis, Forensics, Compliance, Risk Management, Encryption and Social Engineering.
Let’s dive into the details by examining the 11 secondary skills of a Cyber Security Analyst.
Programming
Knowledge of programming languages like Python, Java, or C++ can be beneficial for a Cyber Security Analyst. It helps in automating tasks, developing security tools, and understanding the code behind potential vulnerabilities.
Operating Systems
Familiarity with various operating systems, including Windows, Linux, and macOS, is important. Cyber Security Analysts need to understand the security features and vulnerabilities specific to each OS to effectively protect them.
Cloud Security
With the increasing adoption of cloud services, understanding cloud security is becoming essential. Cyber Security Analysts need to know how to secure data and applications in cloud environments and manage cloud-specific threats.
Firewall Management
Managing and configuring firewalls is a key skill for Cyber Security Analysts. Firewalls act as a barrier between trusted and untrusted networks, and proper management ensures that only legitimate traffic is allowed.
Identity Management
Identity management involves ensuring that the right individuals have access to the right resources. Cyber Security Analysts use this skill to implement and manage authentication and authorization mechanisms, reducing the risk of unauthorized access.
Data Analysis
Data analysis skills help Cyber Security Analysts to interpret and make sense of large volumes of security data. This skill is crucial for identifying patterns, trends, and anomalies that could indicate potential security threats.
Forensics
Digital forensics involves investigating and analyzing digital evidence from security incidents. Cyber Security Analysts use forensic techniques to trace the origin of attacks, understand their impact, and gather evidence for legal proceedings.
Compliance
Understanding regulatory and compliance requirements is important for Cyber Security Analysts. This skill ensures that the organization adheres to legal standards and industry best practices, avoiding potential fines and reputational damage.
Risk Management
Risk management involves identifying, assessing, and prioritizing risks to an organization's information assets. Cyber Security Analysts use this skill to develop strategies to mitigate risks and ensure business continuity.
Encryption
Encryption is the process of converting data into a secure format that can only be read by authorized parties. Cyber Security Analysts use encryption to protect sensitive information from being accessed by unauthorized individuals.
Social Engineering
Understanding social engineering tactics is important for Cyber Security Analysts. This skill helps in recognizing and preventing manipulation techniques used by attackers to gain access to sensitive information.
How to assess Cyber Security Analyst skills and traits
Assessing the skills and traits of a Cyber Security Analyst can be a challenging task, given the wide range of expertise required in this field. From network security to threat analysis, and from incident response to vulnerability assessment, a proficient Cyber Security Analyst must be adept in various domains to effectively safeguard an organization's digital assets.
Traditional resumes and certifications may provide a glimpse into a candidate's background, but they often fall short in revealing the true depth of their capabilities. This is where skills-based assessments come into play. By leveraging targeted assessments, you can gain a clearer understanding of a candidate's proficiency in areas such as malware analysis, cryptography, security auditing, penetration testing, and SIEM management.
For a more streamlined and accurate evaluation process, consider using Adaface on-the-job skill tests. These assessments can help you achieve a 2x improved quality of hires and an 85% reduction in screening time, ensuring that you find the right fit for your cyber security needs.
Let’s look at how to assess Cyber Security Analyst skills with these 5 talent assessments.
CISCO Security Online Test
CISCO Security Online Test evaluates candidates on their understanding of network security concepts and their proficiency with Cisco security products and solutions.
The test assesses knowledge in areas such as CISCO Firewall, VPN, intrusion prevention systems, and security policies. It also examines candidates' abilities to design and implement secure network architectures using Cisco technologies.
Successful candidates demonstrate a thorough understanding of network threats and vulnerabilities, as well as the ability to deploy and manage Cisco security appliances effectively.
Cyber Security Assessment Test
Cyber Security Assessment Test measures a candidate's foundational knowledge in cybersecurity, including operating systems, computer networks, and cloud concepts.
This test evaluates the ability to detect and mitigate security risks such as SQL injections, malware, and various network attacks, and to implement defenses like DDoS protection, firewalls, and cryptography techniques.
Candidates who score well are proficient in setting up cybersecurity defenses and conducting risk assessments to protect against future threats.
Penetration Testing Test
Penetration Testing Test assesses a candidate's skills in identifying and exploiting vulnerabilities in systems and networks ethically.
The test covers areas such as ethical hacking, vulnerability assessment, network security, and web application security, focusing on the ability to conduct thorough penetration tests.
High-scoring individuals are adept at providing actionable recommendations to enhance the security posture of systems and applications.
Cryptography Test
Cryptography Test evaluates a candidate's understanding of cryptography algorithms, digital signatures, and hashing techniques.
It tests candidates on their ability to apply cryptography concepts to secure network communications and data, including encoding, decoding, and the use of various cryptographic algorithms.
Candidates excelling in this test demonstrate a strong grasp of cyber security fundamentals and the application of cryptography in securing information.
Elasticsearch Test
Elasticsearch Test assesses a candidate's ability to design, deploy, and manage Elasticsearch clusters effectively.
The test evaluates skills in configuring search queries, data indexing, and performance optimization, as well as understanding security and data modeling within Elasticsearch environments.
Successful candidates show proficiency in managing and troubleshooting cluster performance issues and scaling Elasticsearch solutions.
Summary: The 9 key Cyber Security Analyst skills and how to test for them
| Cyber Security Analyst skill | How to assess them |
|---|---|
| 1. Network Security | Evaluate the ability to protect and monitor network infrastructure. |
| 2. Threat Analysis | Assess skills in identifying and evaluating potential security threats. |
| 3. Incident Response | Check proficiency in managing and mitigating security incidents. |
| 4. Vulnerability Assessment | Measure capability to identify and address security weaknesses. |
| 5. Malware Analysis | Determine expertise in analyzing and mitigating malware threats. |
| 6. Cryptography | Gauge knowledge in implementing and managing encryption techniques. |
| 7. Security Auditing | Evaluate skills in conducting thorough security audits. |
| 8. Penetration Testing | Assess ability to simulate attacks and identify vulnerabilities. |
| 9. SIEM Management | Check proficiency in managing and configuring SIEM tools. |
Cyber Security Assessment Test
Cyber Security Analyst skills FAQs
What are the key skills required for a Cyber Security Analyst?
Cyber Security Analysts need a diverse set of skills including Network Security, Incident Response, Malware Analysis, Cryptography, and Risk Management. Proficiency in tools for Penetration Testing and SIEM Management is also important.
How can recruiters assess the proficiency in Network Security for a candidate?
Recruiters can assess Network Security skills by examining candidates' experience with firewall configurations, VPN management, and intrusion detection systems. Practical tests or case studies during interviews can also provide insight into their hands-on abilities.
What is the importance of Programming skills in Cyber Security?
Programming skills enable Cyber Security Analysts to automate security solutions, understand and mitigate vulnerabilities in software, and develop tools that can help in securing applications. Languages like Python, JavaScript, and C++ are commonly used.
How does understanding Cloud Security enhance a Cyber Security Analyst's role?
With many organizations moving to cloud-based solutions, understanding Cloud Security is key. Analysts must be adept at securing cloud environments, managing cloud-based firewalls, and ensuring compliance with cloud security protocols.
What role does Data Analysis play in Cyber Security?
Data Analysis helps Cyber Security Analysts identify trends and patterns in data breaches and cyber attacks, enabling them to predict and prevent future threats. Skills in data analytics tools and techniques are therefore highly beneficial.
Why is knowledge of Compliance and Risk Management critical for Cyber Security Analysts?
Compliance ensures that organizations meet legal and regulatory standards which can prevent hefty fines and legal issues. Risk Management involves identifying, evaluating, and prioritizing risks to ensure strategic security planning.
How can a candidate demonstrate expertise in Incident Response during an interview?
Candidates can showcase their Incident Response expertise by discussing specific past experiences where they successfully managed security breaches. They can also discuss strategies they've implemented for rapid threat detection and mitigation.
What are effective ways to evaluate a candidate's skills in Malware Analysis?
Evaluating skills in Malware Analysis can be done through technical interviews that include practical tasks such as analyzing malicious software, identifying its behavior, and suggesting mitigation strategies.

40 min skill tests.
No trick questions.
Accurate shortlisting.
We make it easy for you to find the best candidates in your pipeline with a 40 min skills test.
Try for freeRelated posts
Free resources



