Hiring the right penetration testing expert is crucial for maintaining your organization's cybersecurity posture. To make informed hiring decisions, you need a comprehensive set of interview questions that can effectively gauge a candidate's technical skills, problem-solving abilities, and ethical mindset.
This blog post presents a curated list of penetration testing interview questions and answers, categorized for different experience levels and specific areas of expertise. From basic concepts to advanced methodologies, these questions cover a wide range of topics essential for assessing potential penetration testers.
By using these interview questions, you can identify top talent and build a strong cybersecurity team. Consider combining these questions with a pre-interview penetration testing assessment to streamline your hiring process and ensure you're interviewing the most qualified candidates.
Table of contents
18 basic Penetration Testing interview questions and answers to assess candidates

To properly evaluate candidates for a penetration testing role, it's essential to ask them the right questions. This list of basic Penetration Testing interview questions is designed to help you assess their foundational knowledge and technical skills effectively. For more insights, you can also check out our penetration testing expert job description.
- What is penetration testing, and why is it important for an organization?
- Can you explain the difference between black-box, white-box, and gray-box testing?
- Describe the steps involved in a typical penetration testing methodology.
- What tools do you commonly use for penetration testing, and why?
- How do you ensure that your penetration testing activities do not disrupt normal business operations?
- Can you explain what a vulnerability assessment is and how it differs from penetration testing?
- What are some common vulnerabilities you look for during a penetration test?
- How do you prioritize the vulnerabilities you find during a penetration test?
- Explain how you would report the findings of a penetration test to a non-technical audience.
- What steps do you take to stay updated with the latest security threats and vulnerabilities?
- How do you approach testing web applications differently from network infrastructure?
- Describe a challenging penetration test you have conducted and how you overcame the difficulties.
- What are the legal and ethical considerations you must keep in mind during penetration testing?
- How do you handle situations where you encounter unexpected sensitive data during a test?
- Can you discuss any experience you have with social engineering techniques in penetration testing?
- How do you ensure that your penetration testing process is thorough and covers all potential entry points?
- What strategies do you use for evading detection by security systems during a test?
- How do you validate and verify the effectiveness of security measures after remediation efforts?
6 Penetration Testing interview questions and answers to evaluate junior testers
Ready to put your junior penetration testers through their paces? These carefully curated questions will help you gauge their understanding of key concepts and practical skills. Use this list to assess candidates' foundational knowledge and problem-solving abilities in real-world scenarios. Remember, the goal is to find someone who can think on their feet and grow into the role.
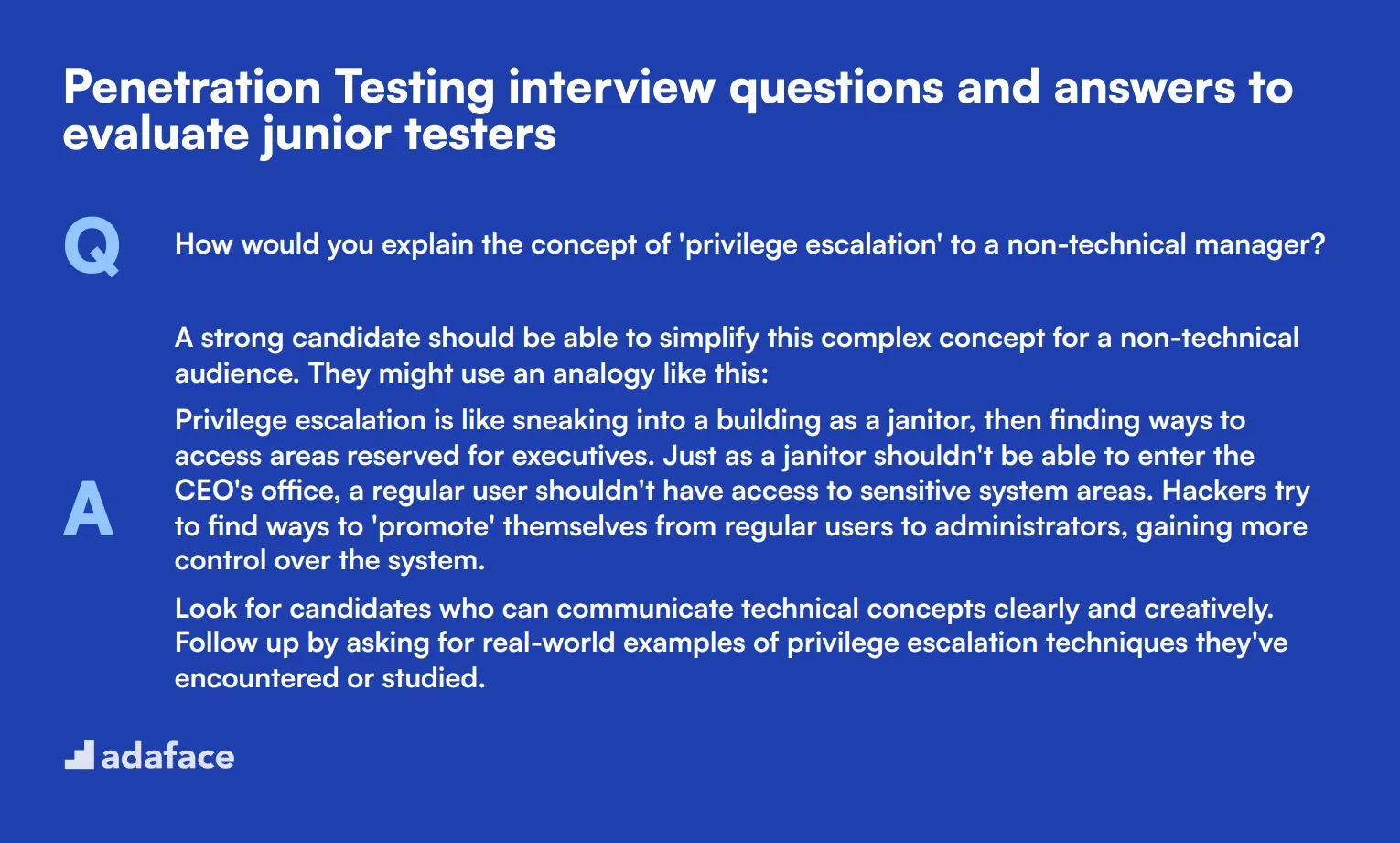
1. How would you explain the concept of 'privilege escalation' to a non-technical manager?
A strong candidate should be able to simplify this complex concept for a non-technical audience. They might use an analogy like this:
Privilege escalation is like sneaking into a building as a janitor, then finding ways to access areas reserved for executives. Just as a janitor shouldn't be able to enter the CEO's office, a regular user shouldn't have access to sensitive system areas. Hackers try to find ways to 'promote' themselves from regular users to administrators, gaining more control over the system.
Look for candidates who can communicate technical concepts clearly and creatively. Follow up by asking for real-world examples of privilege escalation techniques they've encountered or studied.
2. Describe a situation where you would use a 'man-in-the-middle' attack during a penetration test.
A knowledgeable candidate should explain that a man-in-the-middle (MITM) attack is used to intercept communication between two parties. They might describe a scenario like this:
During a penetration test, an MITM attack could be used to assess the security of a company's Wi-Fi network. The tester could set up a rogue access point that mimics the company's legitimate Wi-Fi. When employees connect to this fake network, the tester can intercept and analyze their traffic, potentially capturing sensitive information or credentials.
Look for candidates who emphasize the importance of having proper authorization before conducting such tests. They should also mention the need to handle any captured data ethically and in compliance with privacy regulations.
3. How would you approach testing a web application for SQL injection vulnerabilities?
A competent junior tester should outline a structured approach to testing for SQL injection. They might describe steps such as:
- Identify input fields: Locate all areas where user input is accepted.
- Test with special characters: Input characters like single quotes, double quotes, or semicolons to see if they cause errors.
- Use SQL-specific payloads: Try common SQL injection strings to see if they alter the application's behavior.
- Analyze responses: Look for error messages or unexpected results that might indicate successful injection.
- Verify and document: Confirm any potential vulnerabilities and document findings clearly.
Pay attention to candidates who mention the importance of understanding the underlying database technology and the need for both automated tools and manual testing techniques. A good follow-up question might be about their familiarity with specific SQL injection prevention methods.
4. What steps would you take to ensure the confidentiality of client data during a penetration test?
A responsible candidate should demonstrate a strong commitment to data protection. They might outline steps such as:
- Sign NDAs and confidentiality agreements before starting the engagement.
- Use encrypted communication channels for all client interactions.
- Store any collected data on encrypted, password-protected devices.
- Limit access to test data to only essential team members.
- Securely wipe all client data after the engagement is complete.
- Provide detailed reports only through secure channels.
Look for candidates who emphasize the importance of treating client data with utmost care and following industry best practices for data security. A good follow-up question might be about their familiarity with relevant data protection regulations like GDPR or HIPAA.
5. How would you go about discovering and enumerating services on a target network?
A knowledgeable candidate should describe a methodical approach to network reconnaissance. They might outline steps like:
- Start with passive reconnaissance: Gather publicly available information about the target.
- Perform network scanning: Use tools like Nmap to identify live hosts and open ports.
- Service enumeration: Determine what services are running on open ports.
- Version detection: Identify specific versions of services for potential vulnerabilities.
- OS fingerprinting: Attempt to determine the operating systems in use.
- Document findings: Carefully record all discovered information for later analysis.
Look for candidates who mention the importance of being thorough yet stealthy to avoid detection. They should also be aware of the legal and ethical considerations of network scanning. A good follow-up question might be about specific tools they're familiar with for each step of the process.
6. Can you explain the difference between encoding, encryption, and hashing?
A solid candidate should be able to clearly differentiate between these three concepts:
• Encoding: A reversible process that transforms data into a different format, primarily for data usability or storage. It doesn't provide security. • Encryption: A two-way process that uses an algorithm and a key to scramble data, making it unreadable without the decryption key. It's designed for security. • Hashing: A one-way process that creates a fixed-size output from input data. It's used for data integrity checks and password storage, as it can't be reversed.
Look for candidates who can provide examples of each concept and explain their appropriate use cases in security contexts. A good follow-up question might be about specific algorithms or methods they're familiar with for each process.
12 Penetration Testing interview questions about vulnerabilities

To assess whether candidates possess a deep understanding of identifying and mitigating security weaknesses, consider using these 12 Penetration Testing interview questions about vulnerabilities. These questions will help you gauge their practical knowledge and problem-solving abilities, ensuring they are well-equipped to handle the complexities of the role. For more guidance on what to look for in a penetration testing expert, visit this detailed job description.
- Can you explain what the OWASP Top 10 vulnerabilities are and why they are important?
- How do you identify and exploit cross-site scripting (XSS) vulnerabilities in a web application?
- Describe the process you would use to find and exploit a buffer overflow vulnerability.
- What methods do you use to detect and exploit SQL injection vulnerabilities?
- How do you test for and mitigate the risks associated with insecure deserialization?
- Explain how you would discover and exploit a remote code execution vulnerability.
- How do you identify and address security misconfigurations in a system?
- What approaches do you use to find weak authentication mechanisms in an application?
- How do you handle vulnerabilities that are found in third-party components of a system?
- What techniques do you use to detect and exploit directory traversal vulnerabilities?
- Can you describe how you would exploit an XML External Entity (XXE) vulnerability?
- What steps do you take to identify and exploit file upload vulnerabilities?
6 Penetration Testing interview questions and answers related to tools and methodologies

To gauge a candidate's practical knowledge and approach to penetration testing, consider asking these insightful questions. They're designed to reveal not just technical know-how, but also problem-solving skills and ethical awareness. Use them to spark discussions that illuminate a candidate's real-world readiness for this critical role.
1. How would you approach testing a client's wireless network security?
A strong answer should outline a methodical approach to wireless network testing:
- Reconnaissance: Identify all wireless access points and their configurations
- Scanning: Use tools to capture network traffic and analyze protocols
- Gaining Access: Attempt to crack WEP/WPA keys or exploit vulnerabilities
- Maintaining Access: Test if sustained unauthorized access is possible
- Covering Tracks: Demonstrate how an attacker might hide their activities
- Reporting: Document findings and recommend security improvements
Look for candidates who emphasize the importance of client authorization, discuss specific tools they'd use, and mention potential legal considerations. A great response might also touch on newer threats specific to wireless networks, such as evil twin attacks or Wi-Fi pineapple devices.
2. Describe a situation where you encountered an unusual or custom application during a pentest. How did you approach it?
This question helps assess a candidate's adaptability and problem-solving skills. A strong answer might include:
- Initial reconnaissance to understand the application's purpose and functionality
- Attempts to find documentation or source code for the custom app
- Manual testing to identify potential entry points or vulnerabilities
- Development of custom scripts or tools to test specific functions
- Collaboration with the client to gain more insight into the application
Look for candidates who demonstrate creativity, persistence, and a methodical approach to unfamiliar scenarios. The best responses will highlight the importance of continuous learning and adaptability in the ever-evolving field of cybersecurity.
3. How do you stay informed about new vulnerabilities and attack techniques?
A comprehensive answer should demonstrate a proactive approach to continuous learning:
- Following security blogs, forums, and social media accounts of respected security researchers
- Regularly checking vulnerability databases like CVE and NVD
- Participating in online courses, webinars, and security conferences
- Engaging in capture-the-flag (CTF) competitions and bug bounty programs
- Collaborating with peers and participating in security communities
- Reading academic papers and security whitepapers
Look for candidates who show genuine enthusiasm for the field and have a structured approach to staying updated. The best answers will also mention the importance of practical application of new knowledge, not just passive consumption of information.
4. Can you explain the concept of 'defense in depth' and how it relates to penetration testing?
A strong answer should explain that 'defense in depth' is a cybersecurity strategy that employs multiple layers of security controls to protect an organization's assets. It's based on the principle that no single security measure is perfect, and a combination of defenses is more effective.
In relation to penetration testing, the candidate should highlight:
- Penetration tests help validate the effectiveness of each security layer
- Tests can reveal how well the layers work together to prevent or detect attacks
- Pentesters often try to bypass multiple security controls, simulating sophisticated attacks
- Findings from pentests can help organizations improve their defense-in-depth strategy
Look for answers that demonstrate an understanding of both offensive and defensive security perspectives. The best responses will include examples of how different security layers interact and how penetration testing can reveal gaps in this multi-layered approach.
5. How would you explain the risks and benefits of penetration testing to a non-technical board of directors?
This question assesses the candidate's ability to communicate complex technical concepts to a non-technical audience. A good answer might include:
- Risks: Potential for system disruptions, data exposure, or temporary service interruptions during testing
- Benefits: Identifying vulnerabilities before real attackers do, demonstrating compliance with regulations, and improving overall security posture
Look for candidates who can use analogies or real-world examples to illustrate their points. For instance, they might compare penetration testing to a fire drill or a health check-up. The best answers will also touch on the business impact, such as protecting brand reputation and customer trust, and potentially avoiding costly data breaches.
6. What ethical considerations do you keep in mind when performing social engineering tests?
A comprehensive answer should address several key ethical considerations:
- Obtaining explicit consent from the organization's leadership
- Respecting individual privacy and not exploiting personal vulnerabilities
- Avoiding tactics that could cause undue stress or harm to employees
- Ensuring all data collected is handled securely and destroyed after the test
- Being prepared to immediately reveal the nature of the test if a situation escalates
- Following all relevant laws and regulations
Look for candidates who demonstrate a strong ethical framework and understanding of the potential psychological impact of social engineering tests. The best responses will also mention the importance of clear boundaries and rules of engagement established before the test begins.
7 situational Penetration Testing interview questions with answers for hiring top testers

To determine whether your applicants possess the practical skills needed for real-world challenges, use these situational penetration testing interview questions. They help reveal how candidates think on their feet and solve problems under pressure, ensuring you hire the best of the best.
1. You are in the middle of a penetration test and discover an unknown service running on a client's server. How would you proceed?
First, I would document the discovery and gather as much information as possible about the unknown service. This includes identifying the port number, service version, and any related network traffic. Next, I would research the service to understand any known vulnerabilities or weaknesses associated with it.
After gathering information, I would assess the risk level of the service to the overall security of the system. If the service poses a significant threat, I would immediately notify the client and recommend a course of action, such as patching or disabling the service. For less critical issues, I would include the findings in the final report with appropriate recommendations.
What to look for: Candidates should demonstrate a methodical approach, strong research skills, and the ability to communicate findings effectively. Follow up by asking for examples from their past experiences.
2. During a penetration test, you find that the client's firewall is misconfigured, allowing unnecessary open ports. How do you handle this?
Upon discovering the misconfiguration, I would first verify the extent of the issue by identifying all open ports and the services running on them. I would then cross-check this information with the client's security policies and requirements to determine which ports are unnecessary.
Next, I would prioritize the risks associated with the open ports and create a detailed report outlining the steps needed to correct the misconfiguration. This report would include recommendations for closing unnecessary ports, enhancing monitoring, and implementing stricter firewall rules. I would then communicate these findings to the client and assist them in remediation if needed.
What to look for: Look for clear communication skills, the ability to create actionable reports, and a thorough understanding of firewall configurations. Ask for specific instances where they have dealt with similar issues.
3. Imagine you are performing a penetration test and you accidentally disrupt the client's services. What steps would you take to handle the situation?
First, I would immediately stop the test and assess the extent of the disruption. I would document the actions that led to the disruption and gather any relevant logs or data to understand what went wrong. Then, I would inform the client about the incident, providing them with all the necessary details and an initial assessment of the impact.
Next, I would work with the client's IT team to restore the affected services as quickly as possible, ensuring minimal downtime. Once services are restored, I would conduct a thorough review to identify the root cause of the disruption and implement measures to prevent similar issues in the future. This could include adjusting the testing methodology or improving communication protocols.
What to look for: Candidates should show responsibility, quick problem-solving abilities, and effective communication skills. Follow up by asking how they have handled service disruptions in previous tests.
4. You are asked to perform a penetration test on a client's newly developed web application that has no documentation. How would you approach this task?
Without documentation, my first step would be to perform reconnaissance to gather as much information as possible about the web application. This includes understanding its architecture, technologies used, and functionalities by exploring the application and analyzing its network traffic.
I would then use this information to identify potential attack vectors and plan my testing approach. This involves conducting various tests such as input validation, session management, and authentication checks. Throughout the process, I would document my findings and methodologies to create a comprehensive report for the client. If needed, I would also communicate with the development team to clarify any uncertainties.
What to look for: Look for candidates who exhibit strong analytical skills, resourcefulness, and the ability to work independently. Ask for examples of past projects where they had to work with limited information.
5. During a penetration test, you discover that sensitive data is being transmitted unencrypted. How would you proceed?
Upon discovering unencrypted sensitive data transmission, I would document the specific instances and gather evidence such as network traffic captures. I would then assess the potential impact of this vulnerability on the client's overall security posture and prioritize it based on the sensitivity of the data involved.
Next, I would create a detailed report highlighting the risks associated with unencrypted data transmission and provide recommendations for remediation, such as implementing encryption protocols like HTTPS or VPNs. I would then discuss these findings with the client and offer guidance on how to implement the necessary security measures effectively.
What to look for: Candidates should demonstrate an understanding of encryption protocols, the ability to assess risks, and the skills to provide clear remediation steps. Follow up by asking how they have handled similar situations in the past.
6. If a client asks you to test their internal network, but they have limited access to physical locations, how would you adjust your approach?
In this scenario, I would leverage remote testing techniques to assess the internal network's security. This includes using VPNs or secure remote access tools to connect to the client's network and perform the necessary tests. I would also coordinate with the client's IT team to ensure I have the required access permissions and credentials.
I would focus on identifying vulnerabilities in network configurations, internal services, and endpoint security. Additionally, I would use network scanning tools and techniques to map out the internal network and identify potential attack vectors. Throughout the process, I would maintain clear communication with the client to ensure transparency and address any concerns.
What to look for: Look for candidates who can adapt to remote testing conditions, demonstrate effective use of remote access tools, and maintain strong communication with clients. Ask for examples of past remote testing experiences.
7. You find a critical vulnerability during a penetration test, but the client insists on delaying the fix due to business priorities. How do you handle this situation?
I would start by clearly communicating the severity of the vulnerability and its potential impact on the client's business. This includes providing detailed evidence and examples of how the vulnerability could be exploited by attackers. I would also outline the risks of delaying the fix, such as data breaches or financial losses.
If the client still insists on delaying the fix, I would document their decision and ensure that the vulnerability is included in the final report with appropriate recommendations. Additionally, I would suggest interim measures to mitigate the risk, such as increased monitoring or temporary access controls, until a permanent fix can be implemented.
What to look for: Candidates should show strong communication skills, the ability to convey the importance of security measures, and a pragmatic approach to risk management. Follow up by asking how they have dealt with similar situations in the past.
Which Penetration Testing skills should you evaluate during the interview phase?
While no single interview can fully assess a candidate's capabilities and fit for a role, focusing on core Penetration Testing skills during the interview phase can yield highly informative insights. This approach helps in identifying candidates who are best suited for the demands and challenges of Penetration Testing positions.
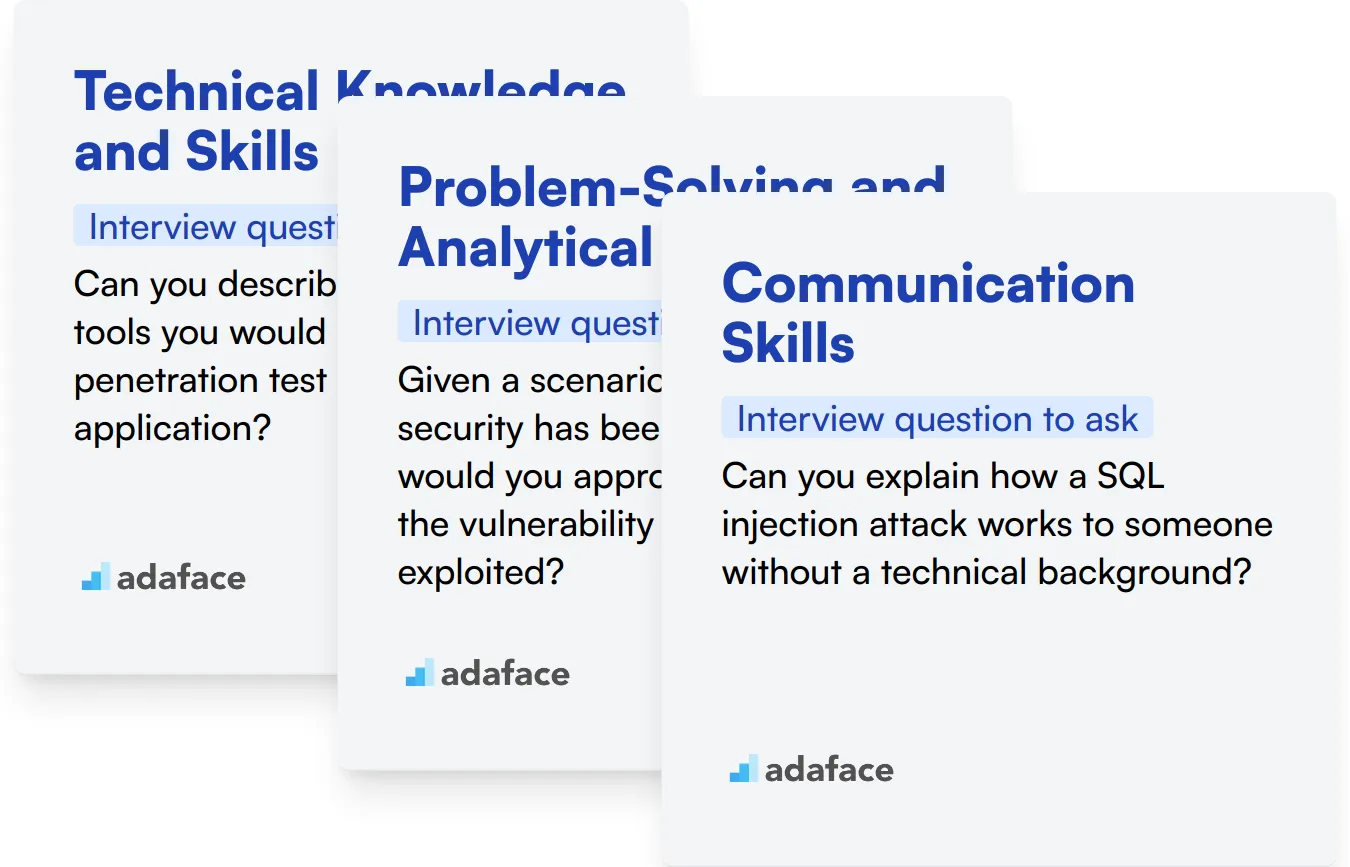
Technical Knowledge and Skills
Technical knowledge is the backbone of Penetration Testing. A deep understanding of systems, networks, and application security is imperative to effectively identify and exploit vulnerabilities.
Consider utilizing a specific assessment test from our library that features relevant MCQs to gauge candidates' foundational knowledge. Our Penetration Testing assessment is designed to filter candidates effectively.
During the interview, it's beneficial to explore the candidate’s practical application of technical skills. A targeted question might help in understanding their hands-on capabilities.
Can you describe the process and tools you would use to carry out a penetration test on a web application?
Listen for a structured testing process, mention of specific tools like Burp Suite or OWASP ZAP, and understanding of both automated and manual testing techniques.
Problem-Solving and Analytical Skills
Penetration Testers need to think like hackers to anticipate and tackle security issues effectively. Analytical skills help them understand complex systems and identify potential security breaches.
To assess this skill, pose problems that require analytical thinking and a methodical approach to breaking down security protocols.
Given a scenario where a system's security has been breached, how would you approach identifying the vulnerability that was exploited?
Look for logical reasoning in their approach to isolating the problem and their methodology in verifying the security hole, reflecting effective analytical skills.
Communication Skills
Effective communication is critical for Penetration Testers, as they must often explain complex technical issues and their implications to non-technical stakeholders.
To evaluate communication skills, ask candidates to explain a technical concept or a previous project experience to a non-technical audience.
Can you explain how a SQL injection attack works to someone without a technical background?
Assess the candidate’s ability to articulate technical jargon in layman’s terms and their capacity to engage the listener by making the information accessible and understandable.
Hire top talent with Penetration Testing skills tests and the right interview questions
When hiring for Penetration Testing roles, it’s important to ensure candidates possess the necessary skills. This assessment will help you identify those who truly stand out in their expertise.
Using skills tests is a highly effective way to evaluate a candidate's capabilities. Consider utilizing our Penetration Testing Test to gain valuable insights into their technical knowledge.
After conducting the test, you can shortlist the most qualified applicants for interviews. This process ensures that you are engaging with candidates who meet your specific requirements.
To take the next step in your hiring journey, visit our online assessment platform to explore more about our tests and sign up for a demo.
Penetration Testing Test
Download Penetration Testing interview questions template in multiple formats
Penetration Testing Interview Questions FAQs
Penetration Testing is a method used to evaluate the security of a system by simulating attacks by a malicious user.
Penetration Testing helps identify and fix security vulnerabilities before they can be exploited by attackers.
A Penetration Tester should have knowledge of networking, system administration, coding, and security tools, among other skills.
Penetration Testing should be conducted regularly, at least annually, or whenever significant changes are made to the system.
Common tools include Nmap, Metasploit, Wireshark, and Burp Suite, among others.

40 min skill tests.
No trick questions.
Accurate shortlisting.
We make it easy for you to find the best candidates in your pipeline with a 40 min skills test.
Try for freeRelated posts
Free resources