As a hiring manager, you're aware that in today's digital landscape, securing your organization's data is more critical than ever. Cyber Security Analysts play a key role in defending against cyber threats and ensuring information security. However, the challenge often lies in finding an analyst who not only has the technical skills but also fits well with your company culture. Many recruiters face difficulties in sourcing the right candidate due to the niche skill set required and a competitive job market.
In this article, we will guide you through the process of hiring a Cyber Security Analyst. We'll cover the role and responsibilities of a Cyber Security Analyst, key skills and qualifications to look for, and effective hiring strategies. Additionally, we provide insights on utilizing platforms like Adaface for pre-employment assessments to streamline your hiring process.
Table of contents
Why Hire a Cyber Security Analyst?
Hiring a Cyber Security Analyst is crucial when your organization faces increasing digital threats. These professionals can help identify vulnerabilities in your systems, implement security measures, and respond to potential breaches.
Consider hiring a Cyber Security Analyst if you're experiencing:
- Frequent security incidents or data breaches
- Difficulty maintaining compliance with industry regulations
- Lack of in-house expertise to manage complex security tools
If you're unsure about committing to a full-time hire, start with a cyber security assessment test to evaluate your current security posture. This can help determine whether you need a full-time analyst or if working with a consultant initially might be more appropriate.
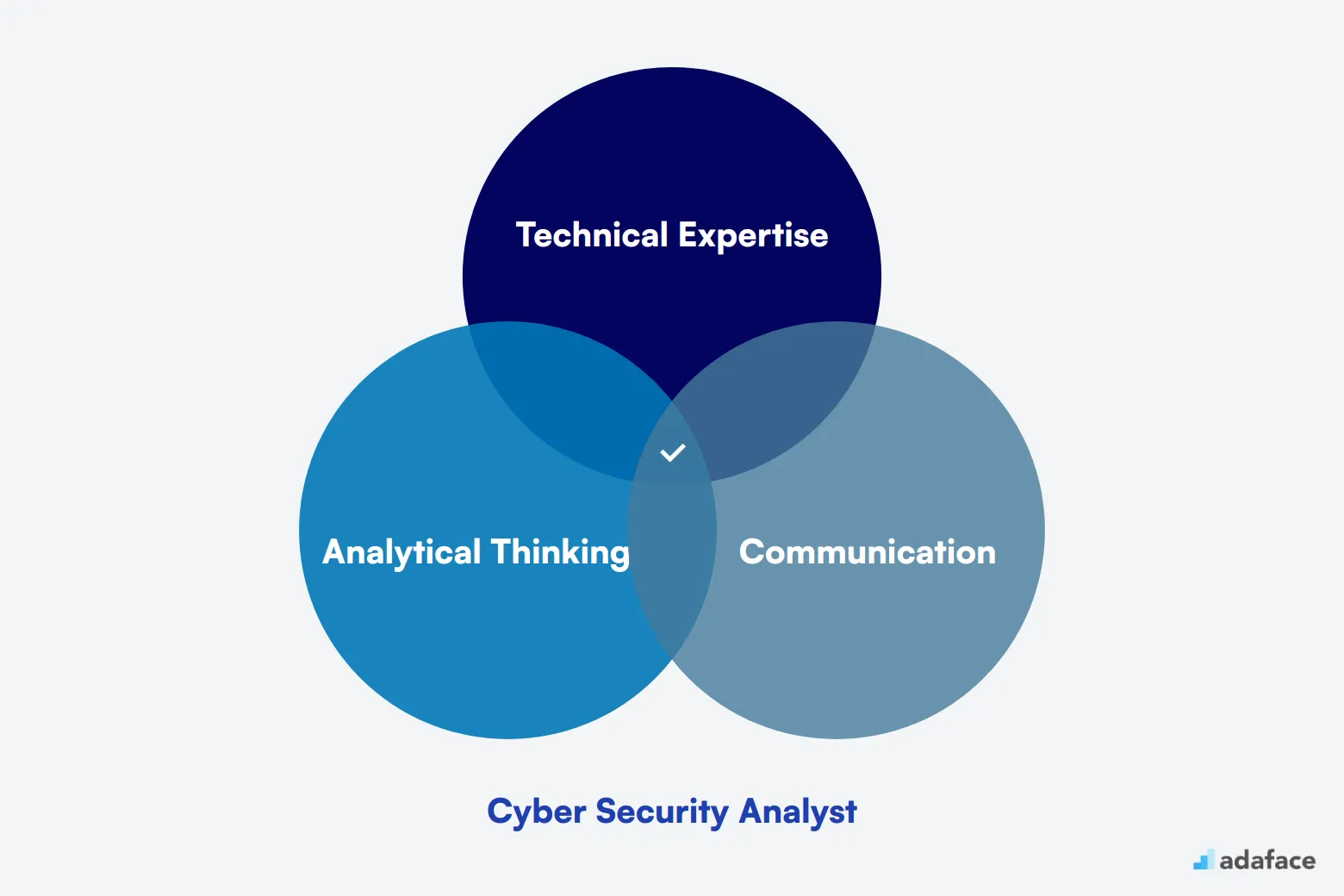
What Does a Cyber Security Analyst Do?
A Cyber Security Analyst plays a key role in protecting an organization's digital assets and information systems. They monitor networks for security breaches, investigate incidents, and implement measures to prevent future attacks.
The day-to-day responsibilities of a Cyber Security Analyst include:
- Monitoring network traffic for suspicious activities
- Conducting vulnerability assessments and risk analyses
- Implementing and maintaining security tools and protocols
- Responding to and investigating security incidents
- Developing security policies and best practices
- Providing security awareness training to employees
- Staying updated on the latest cyber threats and countermeasures
Cyber Security Analyst Hiring Process
Hiring a Cyber Security Analyst requires a structured yet flexible process. The key is to stay focused on finding the right fit for your organization while ensuring an effective timeline.
- Define the role: Craft a clear Cyber Security Analyst job description to attract qualified candidates. Post it on relevant job websites to increase visibility.
- Resume screening: Expect a flow of applications within the first week. Start shortlisting candidates based on their experience and skills that match your requirements.
- Skill assessment: Use online assessment platforms to test technical competencies. This step should take about a week to complete.
- Interviews: Conduct technical and behavioral interviews with shortlisted candidates. This phase narrows down the choice to the top potential hire.
- Offer and onboarding: Once the right candidate is selected, extend an offer and initiate the onboarding process.
Overall, the process generally takes 1-2 months. Expect to refine and expand each stage based on your company’s needs and resources. We'll now explore each step in more detail, providing practical checklists and resources.
Skills and qualifications to look for in a Cyber Security Analyst
Creating an ideal candidate profile for a Cyber Security Analyst can be tricky. The field is vast, and skills requirements can vary based on your company's specific needs. It's important to distinguish between must-have skills and those that are nice-to-have.
Here's a breakdown of key skills and qualifications to consider when hiring a Cyber Security Analyst:
Required Skills and Qualifications:
- Bachelor's degree in Cybersecurity, Computer Science, or related field
- 3+ years of experience in cybersecurity or information security
- Proficiency in network security, intrusion detection, and incident response
- Knowledge of security frameworks (e.g., NIST, ISO 27001)
- Strong analytical and problem-solving skills
Preferred Skills and Qualifications:
- Relevant cybersecurity certifications (e.g., CISSP, CEH, CompTIA Security+)
- Experience with SIEM tools and log analysis
- Familiarity with cloud security concepts and platforms
- Programming skills in languages like Python or JavaScript
- Experience in conducting vulnerability assessments and penetration testing
Remember, the most effective way to evaluate these skills is through a combination of interviews and skill assessment tests. This approach ensures you're getting a well-rounded view of each candidate's abilities.
| Required skills and qualifications | Preferred skills and qualifications |
|---|---|
| Bachelor's degree in Cybersecurity, Computer Science, or related field | Relevant cybersecurity certifications (e.g., CISSP, CEH, CompTIA Security+) |
| 3+ years of experience in cybersecurity or information security | Experience with SIEM tools and log analysis |
| Proficiency in network security, intrusion detection, and incident response | Familiarity with cloud security concepts and platforms |
| Knowledge of security frameworks (e.g., NIST, ISO 27001) | Programming skills in languages like Python or JavaScript |
| Strong analytical and problem-solving skills | Experience in conducting vulnerability assessments and penetration testing |
10 Platforms to Hire Cyber Security Analysts
Now that you have a clear job description ready, it's time to list on various job platforms to source potential candidates. Utilizing specialized job boards can help you find the right talent efficiently and effectively.
Ideal for reaching a wide professional network and sourcing candidates for full-time positions.
Indeed
Comprehensive job board suitable for posting full-time roles and accessing a broad candidate pool.
CyberSecJobs
Specialized job site focused on cybersecurity roles, useful for targeting industry-specific talent.
In addition to the three platforms mentioned earlier, consider using FlexJobs for remote and flexible work opportunities, Upwork for hiring freelance cyber security analysts, and Glassdoor, which also offers company insights and salary information. Moreover, AngelList is ideal for startups looking for dynamic candidates, while Dice focuses on tech roles, including cybersecurity expertise. For broader reach, Monster and Remote.co are also excellent choices for full-time and remote positions, respectively.
Keywords to Look for in a Cyber Security Analyst Resume
Resume screening is a key step in finding the right Cyber Security Analyst. It helps you quickly identify candidates with the most relevant skills and experience before moving to interviews.
When manually screening resumes, focus on key technical and soft skills. Look for terms like 'network security', 'incident response', 'SIEM tools', and certifications like CISSP or CompTIA Security+. Also, pay attention to experience with security frameworks and compliance standards.
AI tools can streamline the screening process. You can use ChatGPT or Claude with a custom prompt to analyze resumes against your job requirements. This can save time and help ensure you don't miss qualified candidates.
TASK: Screen resumes for Cyber Security Analyst role
INPUT: Resumes
OUTPUT:
- Candidate Name
- Matching keywords
- Score (out of 10)
- Shortlist recommendation (Yes/No/Maybe)
KEYWORDS:
- Network security (firewalls, VPNs, IDS/IPS)
- Incident response
- SIEM tools
- Security frameworks (NIST, ISO 27001)
- Certifications (CISSP, CEH, CompTIA Security+)
- Cloud security
- Vulnerability assessment
- Programming (Python, JavaScript)
Recommended skills tests for Cyber Security Analysts
Skills tests are a key part of assessing Cyber Security Analyst candidates. They help you evaluate technical abilities and problem-solving skills objectively. Here are five tests we recommend for screening Cyber Security Analysts:
Cyber Security Test: This test evaluates knowledge of network security, cryptography, and threat detection. It's ideal for assessing a candidate's overall understanding of cyber security principles.
Ethical Hacking Test: Use this assessment to gauge a candidate's ability to identify and exploit vulnerabilities. It helps ensure they can think like an attacker to better defend systems.
Network Engineer Test: A strong grasp of networking is essential for Cyber Security Analysts. This test evaluates understanding of protocols, topologies, and network security concepts.
Linux Test: Many security tools and systems run on Linux. This assessment checks proficiency in Linux commands, file systems, and basic scripting.
Cloud Computing Test: With more organizations moving to the cloud, understanding cloud security is important. This test evaluates knowledge of cloud platforms, services, and security measures.
Recommended Case Study Assignments to Screen Cyber Security Analysts
Case study assignments are a practical way to gauge a candidate's problem-solving skills and on-the-job potential. However, they often pose challenges, such as lengthy completion times and low participation rates, risking the loss of promising candidates. Here are some sample case studies that can effectively assess a candidate's cyber security capabilities.
Network Security Analysis: This assignment involves evaluating a company's network to identify vulnerabilities and recommend security enhancements. It tests the candidate's understanding of network security principles and their ability to apply them in real-world scenarios. You can learn more about the relevant skills in network security.
Incident Response Planning: Candidates are required to create a response plan for a simulated security breach. This task assesses their skills in identifying threats, mitigating risks, and communicating strategies effectively during a crisis. It is an important aspect covered in our cyber security analyst job description.
Vulnerability Assessment: In this case study, candidates perform a vulnerability assessment on a given system, documenting potential weaknesses and suggesting corrective actions. This helps to evaluate their analytical skills and familiarity with tools used for vulnerability analysis, as outlined in our interview questions.
Structuring the Interview Stage for Cyber Security Analysts
After candidates pass the initial cyber security skills tests, it's time for technical interviews to assess their hard skills in depth. While skills tests are great for initial screening, technical interviews help identify the best-fit candidates for the role. Let's explore some key questions to ask during these interviews.
Consider asking: 1) 'How would you respond to a potential data breach?' 2) 'Explain the difference between symmetric and asymmetric encryption.' 3) 'What tools do you use for network monitoring?' 4) 'How do you stay updated on the latest security threats?' 5) 'Describe a time you successfully mitigated a security risk.' These questions help evaluate a candidate's practical knowledge, problem-solving skills, and real-world experience in cyber security.
What's the difference between a Cyber Security Analyst and an Incident Responder?
While both roles are critical in protecting an organization's digital assets, Cyber Security Analysts and Incident Responders have distinct focuses and responsibilities. The main difference lies in their approach to security: proactive versus reactive.
Cyber Security Analysts primarily focus on monitoring and protecting systems. They analyze security alerts, manage vulnerabilities, and conduct risk assessments. Their toolkit includes SIEM, IDS/IPS, and firewalls, and they often hold certifications like CompTIA Security+ or CISSP.
Incident Responders, on the other hand, are the firefighters of the cyber world. They spring into action when a security breach occurs, investigating incidents, mitigating threats, and performing digital forensics. They use specialized forensic tools and sandboxing techniques, and typically hold certifications such as GCFA or GCIH.
The skills required for a Cyber Security Analyst include risk analysis and threat assessment, while Incident Responders need strong incident analysis and digital forensics skills. Cyber Security Analysts usually work in a continuous monitoring environment, whereas Incident Responders thrive in crisis management situations.
In terms of career progression, Cyber Security Analyst roles are often entry to mid-level positions, while Incident Responder roles typically require mid to senior-level experience. Both roles, however, are essential in maintaining a robust cybersecurity posture for any organization.
| Cyber Security Analyst | Incident Responder | |
|---|---|---|
| Primary Focus | Monitor and protect systems | Respond to security incidents |
| Key Skills | Risk analysis, threat assessment | Incident analysis, digital forensics |
| Responsibilities | Analyze security alerts, manage vulnerabilities | Investigate breaches, mitigate threats |
| Tools Used | SIEM, IDS/IPS, Firewalls | Forensic tools, Sandboxing |
| Educational Background | Information Security, Computer Science | Digital Forensics, Cyber Security |
| Typical Certifications | CompTIA Security+, CISSP | GCFA, GCIH |
| Work Environment | Continuous monitoring | Crisis management |
| Experience Level | Entry to Mid-level | Mid to Senior-level |
What are the ranks of Cyber Security Analysts?
The hierarchy of cyber security analysts can often be confusing, especially since roles and responsibilities may overlap. Understanding the ranks helps streamline the hiring process and clarifies job expectations.
• Junior Cyber Security Analyst: This entry-level position is typically responsible for monitoring security systems, assisting in vulnerability assessments, and learning from more experienced analysts. They often work under direct supervision to address basic security incidents.
• Cyber Security Analyst: At this mid-level, analysts take on more responsibility, including conducting threat analyses and implementing security measures. They are expected to have a solid understanding of security protocols and work independently on various projects.
• Senior Cyber Security Analyst: A senior analyst has extensive experience and leads security initiatives within the organization. They mentor junior analysts, conduct advanced threat assessments, and collaborate with other departments to enhance overall security posture.
• Lead Cyber Security Analyst: This rank oversees a team of analysts, ensuring that security operations run smoothly. They are responsible for strategic planning and often communicate with upper management about security risks and recommendations.
• Cyber Security Manager: Managers are responsible for the overall security policies and strategies of an organization. They lead teams of analysts and work closely with executive management to align security objectives with business goals.
• Chief Information Security Officer (CISO): The CISO is the highest-ranking security officer in the organization. They develop and implement information security strategies, oversee all security operations, and serve as the final authority on security-related decisions.
Hire the Right Cyber Security Analysts for Your Team
In this post, we've discussed why hiring a Cyber Security Analyst is important, explained their roles and responsibilities, and outlined key skills and qualifications to look for. We've also covered the hiring process, platforms to find candidates, and how to structure interviews and assignments.
One main takeaway is the significant role of using clear job descriptions and targeted skills tests in hiring the right candidate. Tests like the Cyber Security Test can help you assess technical skills effectively, ensuring that you find the best fit for your team's needs.
Cyber Security Assessment Test
FAQs
A Cyber Security Analyst should have a degree in computer science, information technology, or a related field. Certifications like CISSP, CISM, or CEH are also highly desirable.
Key skills include network security, risk assessment, threat modeling, incident response, and proficiency with security tools and software.
You can use skills assessments like the Adaface Cyber Security Test to evaluate technical skills and conduct structured interviews focusing on problem-solving and analytical abilities.
Platforms such as LinkedIn, Indeed, and specialized job boards like CyberSecJobs are useful for finding qualified Cyber Security Analysts.
While both roles focus on security, an Incident Responder specifically deals with managing and mitigating security breaches, whereas a Cyber Security Analyst focuses on prevention and protection strategies.
Begin with a phone screening to assess cultural fit, followed by technical interviews to evaluate problem-solving skills, and conclude with a case study assignment to gauge practical application of knowledge.

40 min skill tests.
No trick questions.
Accurate shortlisting.
We make it easy for you to find the best candidates in your pipeline with a 40 min skills test.
Try for freeRelated posts
Free resources



