For recruiters and hiring managers, assessing a candidate's cryptography knowledge during interviews can be challenging. The right questions can reveal whether a candidate possesses the necessary skills to protect your organization's information security effectively.
This blog post provides a curated list of cryptography interview questions tailored for various roles and expertise levels. From junior security analysts to senior security engineers, you'll find questions to evaluate candidates' knowledge in encryption techniques, cryptographic protocols, and practical scenarios.
Using these questions will help you identify top talent capable of safeguarding your digital assets. To streamline your hiring process further, consider utilizing specialized pre-employment assessments before conducting interviews.
Table of contents
10 common Cryptography interview questions to ask your candidates

To assess whether candidates possess the critical knowledge and skills in cryptography, use these interview questions as a guide. They can help you evaluate their understanding of fundamental concepts and practical applications in security. This is particularly useful for roles like a Cyber Security Analyst.
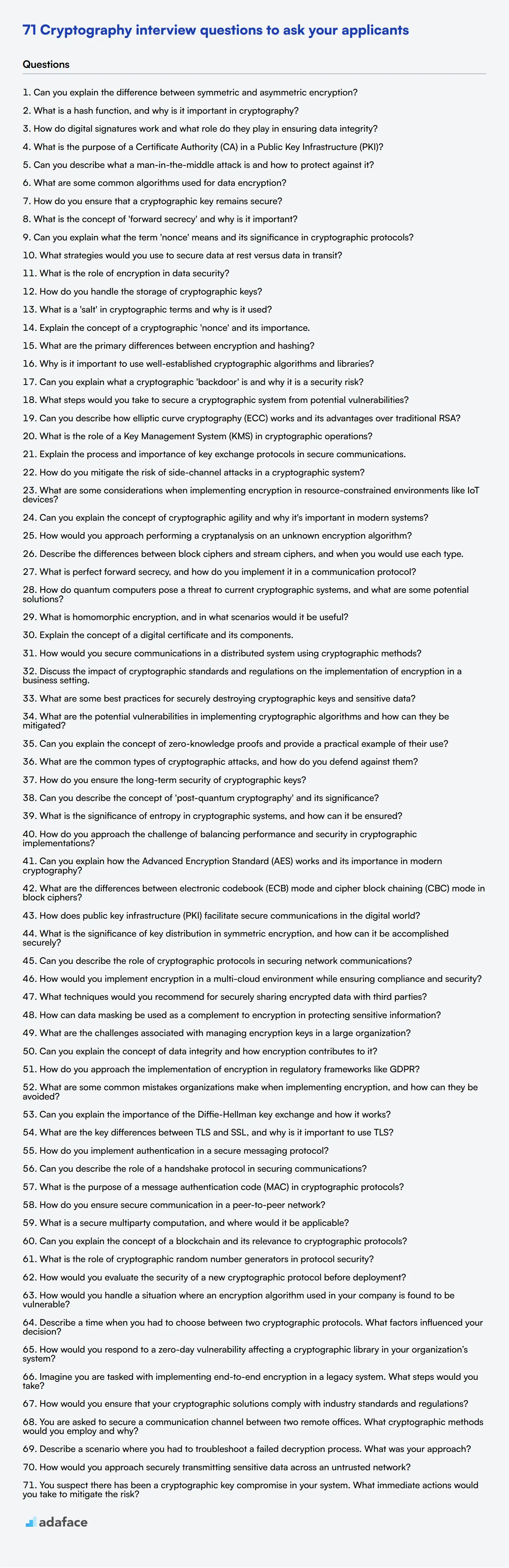
- Can you explain the difference between symmetric and asymmetric encryption?
- What is a hash function, and why is it important in cryptography?
- How do digital signatures work and what role do they play in ensuring data integrity?
- What is the purpose of a Certificate Authority (CA) in a Public Key Infrastructure (PKI)?
- Can you describe what a man-in-the-middle attack is and how to protect against it?
- What are some common algorithms used for data encryption?
- How do you ensure that a cryptographic key remains secure?
- What is the concept of 'forward secrecy' and why is it important?
- Can you explain what the term 'nonce' means and its significance in cryptographic protocols?
- What strategies would you use to secure data at rest versus data in transit?
8 Cryptography interview questions and answers to evaluate junior security analysts

To ensure your junior security analyst candidates have a fundamental understanding of cryptography, use these questions in your interviews. They will help you evaluate their knowledge and problem-solving skills without getting overly technical.
1. What is the role of encryption in data security?
Encryption is the process of converting plaintext into ciphertext to prevent unauthorized access. It plays a crucial role in data security by ensuring that sensitive information remains confidential and is only accessible to those with the correct decryption key.
An ideal candidate should emphasize the importance of encryption in protecting data both in transit and at rest. They should also mention how encryption supports compliance with various data protection regulations.
2. How do you handle the storage of cryptographic keys?
Cryptographic keys should be stored in a secure manner to prevent unauthorized access. This can include using hardware security modules (HSMs), secure key management services, or encrypted storage solutions.
Look for candidates who demonstrate an understanding of the importance of key management policies and practices, such as regular key rotation and using separate keys for different purposes.
3. What is a 'salt' in cryptographic terms and why is it used?
A 'salt' is a random value added to a password before it is hashed. This ensures that even if two users have the same password, their hashed values will be different, which makes it harder for attackers to use precomputed tables (rainbow tables) to crack the passwords.
Candidates should highlight the importance of using a unique salt for each password and explain how this practice increases the security of stored passwords.
4. Explain the concept of a cryptographic 'nonce' and its importance.
A nonce (number used once) is a random or pseudo-random value that is used only once in cryptographic communication. It ensures that each encryption operation is unique, preventing replay attacks and ensuring message integrity.
Strong responses will include examples of where nonces are used, such as in authentication protocols, and discuss their role in preventing replay attacks.
5. What are the primary differences between encryption and hashing?
Encryption is a reversible process used to protect the confidentiality of data, meaning encrypted data can be decrypted back to its original form. Hashing, on the other hand, is a one-way function that converts data into a fixed-size string of characters, which cannot be reversed to obtain the original data.
An ideal candidate will point out that encryption is used for data confidentiality, whereas hashing is primarily used for data integrity and verification, such as in ensuring that files have not been tampered with.
6. Why is it important to use well-established cryptographic algorithms and libraries?
Using well-established cryptographic algorithms and libraries is crucial because they have been extensively tested and reviewed by the security community. This reduces the risk of vulnerabilities that can be exploited by attackers.
Candidates should emphasize that creating custom cryptographic algorithms is risky and often leads to flawed implementations. They should also mention the importance of staying updated with the latest security patches for these libraries.
7. Can you explain what a cryptographic 'backdoor' is and why it is a security risk?
A cryptographic 'backdoor' is a hidden method for bypassing the normal authentication or encryption processes in a system, allowing unauthorized access to data. Backdoors are intentionally added by developers and can be exploited by attackers if discovered.
Strong candidates will discuss the ethical and security implications of backdoors, emphasizing that they undermine the trust and integrity of cryptographic systems.
8. What steps would you take to secure a cryptographic system from potential vulnerabilities?
Securing a cryptographic system involves multiple steps, including regular software updates, using strong and up-to-date cryptographic algorithms, implementing proper key management practices, and conducting regular security audits and penetration testing.
Look for responses that demonstrate a comprehensive approach to security, including staying informed about the latest vulnerabilities and patches, and applying best practices in cryptographic implementations.
15 intermediate Cryptography interview questions and answers to ask mid-tier security consultants

To gauge the expertise of mid-tier security consultants, utilize these intermediate Cryptography interview questions. This list helps identify candidates who possess a deeper understanding of cryptographic principles and can effectively address complex security challenges in roles such as cyber security analyst.
- Can you describe how elliptic curve cryptography (ECC) works and its advantages over traditional RSA?
- What is the role of a Key Management System (KMS) in cryptographic operations?
- Explain the process and importance of key exchange protocols in secure communications.
- How do you mitigate the risk of side-channel attacks in a cryptographic system?
- What are some considerations when implementing encryption in resource-constrained environments like IoT devices?
- Can you explain the concept of cryptographic agility and why it's important in modern systems?
- How would you approach performing a cryptanalysis on an unknown encryption algorithm?
- Describe the differences between block ciphers and stream ciphers, and when you would use each type.
- What is perfect forward secrecy, and how do you implement it in a communication protocol?
- How do quantum computers pose a threat to current cryptographic systems, and what are some potential solutions?
- What is homomorphic encryption, and in what scenarios would it be useful?
- Explain the concept of a digital certificate and its components.
- How would you secure communications in a distributed system using cryptographic methods?
- Discuss the impact of cryptographic standards and regulations on the implementation of encryption in a business setting.
- What are some best practices for securely destroying cryptographic keys and sensitive data?
7 advanced Cryptography interview questions and answers to evaluate senior security engineers

When it comes to evaluating senior security engineers, asking the right questions can make all the difference. This list of advanced cryptography interview questions will help you assess candidates' deep understanding and practical application of cryptographic principles and practices, ensuring you hire the best talent for your team.
1. What are the potential vulnerabilities in implementing cryptographic algorithms and how can they be mitigated?
Cryptographic algorithms can be vulnerable due to poor implementation practices, side-channel attacks, and outdated algorithms. For instance, if the implementation leaks timing information, attackers can perform timing attacks to deduce the secret key.
Mitigation strategies include adhering to best practices such as constant-time implementations, regularly updating cryptographic libraries to avoid deprecated algorithms, and performing thorough code reviews and testing. Additionally, using well-vetted libraries can reduce the risk of introducing vulnerabilities.
Look for candidates who emphasize the importance of secure coding practices, staying updated on cryptographic research, and applying layered security measures to safeguard cryptographic implementations.
2. Can you explain the concept of zero-knowledge proofs and provide a practical example of their use?
Zero-knowledge proofs are cryptographic methods that allow one party to prove to another party that a statement is true without revealing any information beyond the truth of the statement itself. They are used to enhance privacy and security in various applications.
A practical example is in authentication systems where a user can prove they know a password without actually transmitting the password itself. This reduces the risk of password interception during transmission.
Ideal candidates should explain the basic concept clearly and provide relevant examples, showcasing their understanding of the practical applications and benefits of zero-knowledge proofs in enhancing security.
3. What are the common types of cryptographic attacks, and how do you defend against them?
Common cryptographic attacks include brute force attacks, dictionary attacks, replay attacks, and side-channel attacks. Each type exploits different weaknesses in cryptographic systems.
Defensive strategies include using strong, unpredictable keys to counter brute force and dictionary attacks, employing nonce and timestamp mechanisms to prevent replay attacks, and implementing constant-time algorithms to mitigate side-channel attacks.
Candidates should demonstrate a comprehensive understanding of various attack vectors and articulate specific defense mechanisms, emphasizing the importance of a multi-layered security approach.
4. How do you ensure the long-term security of cryptographic keys?
Ensuring the long-term security of cryptographic keys involves several practices such as regular key rotation, using hardware security modules (HSMs), and implementing strict access controls to limit key exposure.
Another critical aspect is monitoring for any signs of key compromise and having protocols in place for immediate key revocation and replacement if a breach is detected.
Candidates should talk about their experience with key management systems and highlight the importance of a proactive approach in maintaining the integrity and confidentiality of cryptographic keys over time.
5. Can you describe the concept of 'post-quantum cryptography' and its significance?
Post-quantum cryptography refers to cryptographic algorithms that are secure against the potential threats posed by quantum computers, which could break many of the classical cryptographic systems in use today.
The significance lies in ensuring that data remains secure even in a future where quantum computers are powerful enough to solve problems that are currently computationally infeasible. This involves developing and implementing new algorithms that can withstand quantum attacks.
Look for candidates who are knowledgeable about the current state of post-quantum cryptography research and who understand the importance of preparing for future technological advancements to protect sensitive data.
6. What is the significance of entropy in cryptographic systems, and how can it be ensured?
Entropy is a measure of randomness, and it is crucial for generating secure cryptographic keys. High entropy ensures that keys are unpredictable and resistant to brute force attacks.
Ensuring entropy can be achieved by using hardware-based random number generators (RNGs), which are generally more secure than software-based RNGs. Additionally, combining multiple sources of entropy can enhance the overall randomness.
Candidates should highlight the importance of entropy in cryptographic security and discuss specific methods and tools they use to guarantee sufficient entropy in key generation processes.
7. How do you approach the challenge of balancing performance and security in cryptographic implementations?
Balancing performance and security involves choosing the right cryptographic algorithms and protocols that provide adequate security without significantly compromising system performance. This often requires a nuanced understanding of the trade-offs involved.
Strategies include using efficient algorithms like elliptic curve cryptography (ECC) for key exchange, optimizing cryptographic computations, and employing hardware accelerators where appropriate.
Ideal candidates should discuss their experience with performance tuning in cryptographic systems and provide examples of how they have achieved an optimal balance in past projects, demonstrating both security expertise and practical implementation skills.
12 Cryptography interview questions about encryption techniques

To assess candidates' knowledge of encryption techniques, use this list of targeted questions. They will help you gauge the applicant's understanding of essential concepts and practical applications relevant to roles like a cyber security engineer.
- Can you explain how the Advanced Encryption Standard (AES) works and its importance in modern cryptography?
- What are the differences between electronic codebook (ECB) mode and cipher block chaining (CBC) mode in block ciphers?
- How does public key infrastructure (PKI) facilitate secure communications in the digital world?
- What is the significance of key distribution in symmetric encryption, and how can it be accomplished securely?
- Can you describe the role of cryptographic protocols in securing network communications?
- How would you implement encryption in a multi-cloud environment while ensuring compliance and security?
- What techniques would you recommend for securely sharing encrypted data with third parties?
- How can data masking be used as a complement to encryption in protecting sensitive information?
- What are the challenges associated with managing encryption keys in a large organization?
- Can you explain the concept of data integrity and how encryption contributes to it?
- How do you approach the implementation of encryption in regulatory frameworks like GDPR?
- What are some common mistakes organizations make when implementing encryption, and how can they be avoided?
10 Cryptography interview questions about cryptographic protocols

To ensure candidates have a solid grasp of cryptographic protocols, use these targeted questions during interviews. They can help gauge an applicant's depth of knowledge and practical application in real-world scenarios, especially for roles like a Cyber Security Engineer.
- Can you explain the importance of the Diffie-Hellman key exchange and how it works?
- What are the key differences between TLS and SSL, and why is it important to use TLS?
- How do you implement authentication in a secure messaging protocol?
- Can you describe the role of a handshake protocol in securing communications?
- What is the purpose of a message authentication code (MAC) in cryptographic protocols?
- How do you ensure secure communication in a peer-to-peer network?
- What is a secure multiparty computation, and where would it be applicable?
- Can you explain the concept of a blockchain and its relevance to cryptographic protocols?
- What is the role of cryptographic random number generators in protocol security?
- How would you evaluate the security of a new cryptographic protocol before deployment?
9 situational Cryptography interview questions for hiring top security experts

To identify top security talent, it's crucial to ask the right situational cryptography questions. These questions help you evaluate a candidate's problem-solving skills and practical experience in real-world scenarios. For more tailored roles, such as a chief information security officer, these questions are invaluable for finding the right fit.
- How would you handle a situation where an encryption algorithm used in your company is found to be vulnerable?
- Describe a time when you had to choose between two cryptographic protocols. What factors influenced your decision?
- How would you respond to a zero-day vulnerability affecting a cryptographic library in your organization’s system?
- Imagine you are tasked with implementing end-to-end encryption in a legacy system. What steps would you take?
- How would you ensure that your cryptographic solutions comply with industry standards and regulations?
- You are asked to secure a communication channel between two remote offices. What cryptographic methods would you employ and why?
- Describe a scenario where you had to troubleshoot a failed decryption process. What was your approach?
- How would you approach securely transmitting sensitive data across an untrusted network?
- You suspect there has been a cryptographic key compromise in your system. What immediate actions would you take to mitigate the risk?
Which Cryptography skills should you evaluate during the interview phase?
While it's impossible to fully gauge a candidate's capabilities in a single interview, focusing on key cryptographic skills can provide valuable insights. These essential skill sets not only assess technical proficiency but also determine a candidate's readiness for the role.

Understanding of Encryption Techniques
A solid understanding of encryption techniques is central to any cryptography role. These skills ensure the candidate can secure data effectively, a primary function in protecting sensitive information.
To accurately assess this skill before an interview, consider administering an MCQ test focused on encryption techniques. For a thorough and tailored assessment, our Cryptography test could be a valuable tool.
During the interview, present specific questions that delve into their practical knowledge and application abilities. Here's an example:
Can you explain the difference between symmetric and asymmetric encryption, and provide an example of when each might be used?
Look for clear explanations that demonstrate understanding of key terms and practical applications. A good answer will include real-world scenarios where each encryption type is most effective.
Knowledge of Cryptographic Protocols
Cryptographic protocols are vital for secure communications in networks. Candidates must display a deep understanding of various protocols to design and implement secure systems.
Utilize an MCQ test to evaluate this knowledge area. Candidates can be effectively pre-screened using our specialized tests such as the Cyber Security test.
To explore this skill in interviews, consider asking the following question:
Describe how SSL/TLS works and mention how it differs from other security protocols.
Expect detailed explanations on SSL/TLS operations and comparisons that highlight their security features against others.
Problem Solving in Cryptographic Contexts
Problem-solving in cryptographic contexts involves innovation and analytical thinking to secure data and solve related challenges. This skill is indicative of a candidate's ability to handle complex and unexpected issues effectively.
To assess problem-solving skills, ask them to address hypothetical scenarios. For example:
How would you approach a situation where you need to secure a legacy system that does not support modern cryptographic standards?
The best responses will show a strategic approach, considering constraints and proposing viable, secure solutions.
Tips for Effective Cryptography Interviews
Before putting your newfound knowledge to use, consider these tips to make your cryptography interviews more effective and insightful.
1. Implement pre-interview skills assessments
Start by using skills tests to evaluate candidates' technical knowledge before the interview. This approach helps you focus on the most promising candidates and tailor your interview questions.
For cryptography roles, consider using IT security tests that include cryptography modules. These assessments can gauge candidates' understanding of encryption algorithms, key management, and cryptographic protocols.
By implementing pre-interview assessments, you can save time and resources. You'll be able to identify candidates with the right technical skills and spend more time during the interview exploring their problem-solving abilities and practical experience.
2. Prepare a balanced set of interview questions
Compile a mix of technical and practical questions to assess both theoretical knowledge and real-world application skills. Focus on key areas such as encryption techniques, cryptographic protocols, and security best practices.
Include questions that evaluate the candidate's ability to think critically about security challenges. Consider adding problem-solving questions to assess their analytical skills in cryptography-related scenarios.
Don't forget to assess soft skills that are important for security roles. Include questions about teamwork, communication, and ethical considerations in cryptography and security.
3. Ask probing follow-up questions
Prepare follow-up questions to dig deeper into candidates' responses. This technique helps you distinguish between superficial knowledge and true expertise in cryptography.
For example, if you ask about symmetric encryption algorithms, a follow-up question might be, "Can you explain a scenario where AES might be preferred over 3DES?" This probes the candidate's understanding of algorithm strengths and practical applications.
Download Cryptography interview questions template in multiple formats
Cryptography Interview Questions FAQs
Ask about encryption techniques, cryptographic protocols, and situational scenarios. Include a mix of basic, intermediate, and advanced questions based on the role.
Use a combination of theoretical questions, practical scenarios, and problem-solving tasks. Assess their understanding of both fundamental concepts and current trends in the field.
Yes, junior roles focus more on basic concepts and tools, while senior roles involve complex scenarios, advanced techniques, and strategic thinking in Cryptography.
The number can vary, but aim for 5-10 well-chosen questions that cover various aspects of Cryptography relevant to the role you're hiring for.

40 min skill tests.
No trick questions.
Accurate shortlisting.
We make it easy for you to find the best candidates in your pipeline with a 40 min skills test.
Try for freeRelated posts
Free resources