Test Duration
30 minsDifficulty Level
Moderate
Questions
- 6 Windows Administration MCQs
- 5 PowerShell MCQs
- 4 Computer Networks MCQs
Availability
Ready to useThe Windows System Administration Online Test uses scenario-based MCQs to evaluate candidates on their understanding of core Windows system administration concepts such as Active Directory, group policy management, network services, and system monitoring. Additionally, the test may assess the candidate's knowledge of scripting languages, server virtualization, and disaster recovery. The test aims to evaluate the candidate's ability to effectively manage Windows-based enterprise environments.
Covered skills:
Test Duration
30 minsDifficulty Level
Moderate
Questions
Availability
Ready to useThe Windows System Administration Online Test helps recruiters and hiring managers identify qualified candidates from a pool of resumes, and helps in taking objective hiring decisions. It reduces the administrative overhead of interviewing too many candidates and saves time by filtering out unqualified candidates at the first step of the hiring process.
The test screens for the following skills that hiring managers look for in candidates:
Use Adaface tests trusted by recruitment teams globally. Adaface skill assessments measure on-the-job skills of candidates, providing employers with an accurate tool for screening potential hires.
We have a very high focus on the quality of questions that test for on-the-job skills. Every question is non-googleable and we have a very high bar for the level of subject matter experts we onboard to create these questions. We have crawlers to check if any of the questions are leaked online. If/ when a question gets leaked, we get an alert. We change the question for you & let you know.
How we design questionsThese are just a small sample from our library of 15,000+ questions. The actual questions on this Windows System Administration Online Test will be non-googleable.
| 🧐 Question | |||||
|---|---|---|---|---|---|
Medium Active Directory Replication Issues | Solve | ||||
Medium Configuring Network Services | Solve | ||||
Medium Remote access policy | Solve | ||||
Medium Security log file | Solve | ||||
Medium Dynamic Function Invocation | Solve | ||||
Medium Error Handling with Try-Catch-Finally | Solve | ||||
Hard Execution Policy Bypass | Solve | ||||
Medium Logging with Transcript | Solve | ||||
Medium Nested Runspaces | Solve | ||||
Medium Mac address and IP on router hop | Solve | ||||
Easy MX Record, DMARC and Email Authentication | Solve | ||||
Medium Remote network resources | Solve | ||||
Medium SSL Certificate Expiry | Solve | ||||
| 🧐 Question | 🔧 Skill | ||
|---|---|---|---|
Medium Active Directory Replication Issues | 2 mins Windows Administration | Solve | |
Medium Configuring Network Services | 2 mins Windows Administration | Solve | |
Medium Remote access policy | 2 mins Windows Administration | Solve | |
Medium Security log file | 2 mins Windows Administration | Solve | |
Medium Dynamic Function Invocation | 2 mins PowerShell | Solve | |
Medium Error Handling with Try-Catch-Finally | 2 mins PowerShell | Solve | |
Hard Execution Policy Bypass | 3 mins PowerShell | Solve | |
Medium Logging with Transcript | 2 mins PowerShell | Solve | |
Medium Nested Runspaces | 3 mins PowerShell | Solve | |
Medium Mac address and IP on router hop | 2 mins Computer Networks | Solve | |
Easy MX Record, DMARC and Email Authentication | 2 mins Computer Networks | Solve | |
Medium Remote network resources | 3 mins Computer Networks | Solve | |
Medium SSL Certificate Expiry | 2 mins Computer Networks | Solve |
| 🧐 Question | 🔧 Skill | 💪 Difficulty | ⌛ Time | ||
|---|---|---|---|---|---|
Active Directory Replication Issues | Windows Administration | Medium | 2 mins | Solve | |
Configuring Network Services | Windows Administration | Medium | 2 mins | Solve | |
Remote access policy | Windows Administration | Medium | 2 mins | Solve | |
Security log file | Windows Administration | Medium | 2 mins | Solve | |
Dynamic Function Invocation | PowerShell | Medium | 2 mins | Solve | |
Error Handling with Try-Catch-Finally | PowerShell | Medium | 2 mins | Solve | |
Execution Policy Bypass | PowerShell | Hard | 3 mins | Solve | |
Logging with Transcript | PowerShell | Medium | 2 mins | Solve | |
Nested Runspaces | PowerShell | Medium | 3 mins | Solve | |
Mac address and IP on router hop | Computer Networks | Medium | 2 mins | Solve | |
MX Record, DMARC and Email Authentication | Computer Networks | Easy | 2 mins | Solve | |
Remote network resources | Computer Networks | Medium | 3 mins | Solve | |
SSL Certificate Expiry | Computer Networks | Medium | 2 mins | Solve |
With Adaface, we were able to optimise our initial screening process by upwards of 75%, freeing up precious time for both hiring managers and our talent acquisition team alike!
Brandon Lee, Head of People, Love, Bonito
It's very easy to share assessments with candidates and for candidates to use. We get good feedback from candidates about completing the tests. Adaface are very responsive and friendly to deal with.
Kirsty Wood, Human Resources, WillyWeather
We were able to close 106 positions in a record time of 45 days! Adaface enables us to conduct aptitude and psychometric assessments seamlessly. My hiring managers have never been happier with the quality of candidates shortlisted.
Amit Kataria, CHRO, Hanu
We evaluated several of their competitors and found Adaface to be the most compelling. Great library of questions that are designed to test for fit rather than memorization of algorithms.
Swayam Narain, CTO, Affable
The Adaface test library features 500+ tests to enable you to test candidates on all popular skills- everything from programming languages, software frameworks, devops, logical reasoning, abstract reasoning, critical thinking, fluid intelligence, content marketing, talent acquisition, customer service, accounting, product management, sales and more.
The Windows System Administration Online Test is designed to evaluate a candidate’s skills in managing Windows servers and networks. It is used by recruiters to identify professionals proficient in Windows System Administration, Active Directory, Group Policy, and other related skills.
Yes, recruiters can request a custom test that includes both Windows System Administration and Networking questions. Check out the Network Engineer Test for more information on how we assess networking skills.
The test covers various topics including Windows System Administration, Active Directory, Group Policy, Windows Server, Networking, PowerShell Scripting, and Server Security. Senior roles are assessed on skills such as deploying DNS services, configuring network protocols, and securing Windows servers.
We recommend using this test as a pre-screening tool at the start of your hiring process. Add a link to the assessment in your job post or invite candidates via email. This helps in identifying skilled candidates early and faster.
Yes, you can combine Windows Administration and PowerShell questions in a single test. This combination helps in evaluating a candidate's ability to manage and automate tasks in a Windows environment. Check out the PowerShell Online Test for more details.
Here are some main System Administration tests:
Yes, absolutely. Custom assessments are set up based on your job description, and will include questions on all must-have skills you specify. Here's a quick guide on how you can request a custom test.
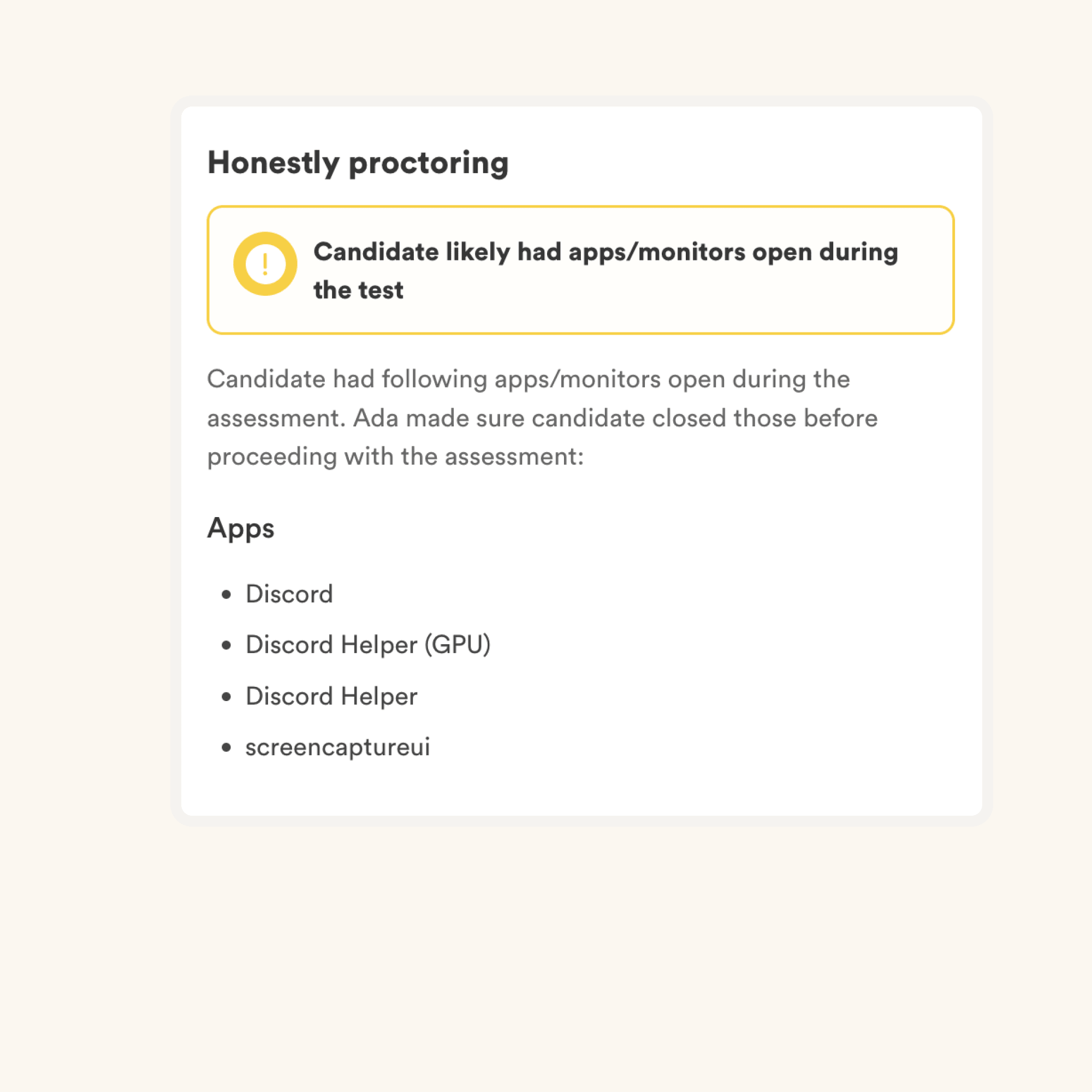
We have the following anti-cheating features in place:
Read more about the proctoring features.
The primary thing to keep in mind is that an assessment is an elimination tool, not a selection tool. A skills assessment is optimized to help you eliminate candidates who are not technically qualified for the role, it is not optimized to help you find the best candidate for the role. So the ideal way to use an assessment is to decide a threshold score (typically 55%, we help you benchmark) and invite all candidates who score above the threshold for the next rounds of interview.
Each Adaface assessment is customized to your job description/ ideal candidate persona (our subject matter experts will pick the right questions for your assessment from our library of 10000+ questions). This assessment can be customized for any experience level.
Yes, it makes it much easier for you to compare candidates. Options for MCQ questions and the order of questions are randomized. We have anti-cheating/ proctoring features in place. In our enterprise plan, we also have the option to create multiple versions of the same assessment with questions of similar difficulty levels.
No. Unfortunately, we do not support practice tests at the moment. However, you can use our sample questions for practice.
You can check out our pricing plans.
Yes, you can sign up for free and preview this test.
Here is a quick guide on how to request a custom assessment on Adaface.